Tool/software:
Dear TI,
Could you let me know how to check reset reason ?
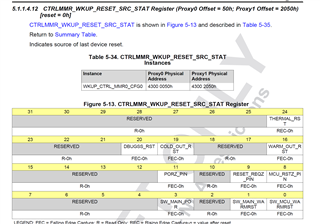
When I check CTRLMMR_WKUP_RST_STAT Register, it is 0x00010001 even after power on reset
root@j7200-evm:~# devmem2 0x43018178
/dev/mem opened.
Memory mapped at address 0xffffb348f000.
Read at address 0x43018178 (0xffffb348f178): 0x00010001
Is there any register which I can distinguish below reset reason ?
- warm reset
- power on reset
- watchdog reset
BR
Jace