Other Parts Discussed in Thread: AM62L
Tool/software:
Hi TI Community,
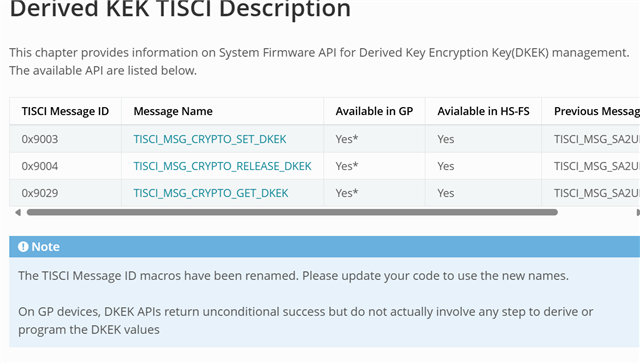
After upgrading the AM62x SDK from version 8.6 to 10.01, we encountered an OP-TEE RPMB secure storage error ("RPMB verification failed"). During debugging, we discovered that the DKEK values differ between the old and new SDKs, leading to the verification failure.
报错日志如下:
D/TC:? 0 ldelf_load_ldelf:110 ldelf load address 0x40007000 D/LD: ldelf:142 Loading TS 8c2e0728-a3fb-4ccc-96b0-9a6498db1aec F/TC:? 0 trace_syscall:147 syscall #3 (syscall_get_property) F/TC:? 0 trace_syscall:147 syscall #5 (syscall_open_ta_session) D/TC:? 0 ldelf_syscall_open_bin:163 Lookup user TA ELF 8c2e0728-a3fb-4ccc-96b0-9a6498db1aec (REE) D/TC:? 0 ldelf_syscall_open_bin:167 res=0 F/TC:? 0 trace_syscall:147 syscall #7 (syscall_invoke_ta_command) F/TC:? 0 trace_syscall:147 syscall #11 (syscall_mask_cancellation) F/TC:? 0 trace_syscall:147 syscall #7 (syscall_invoke_ta_command) F/TC:? 0 trace_syscall:147 syscall #3 (syscall_get_property) F/TC:? 0 trace_syscall:147 syscall #8 (syscall_check_access_rights) F/TC:? 0 trace_syscall:147 syscall #8 (syscall_check_access_rights) D/TC:? 0 legacy_rpmb_init:1142 Trying legacy RPMB init D/TC:? 0 rpmb_set_dev_info:1111 RPMB: Syncing device information D/TC:? 0 rpmb_set_dev_info:1113 RPMB: RPMB size is 32*128 KB D/TC:? 0 rpmb_set_dev_info:1114 RPMB: Reliable Write Sector Count is 1 D/TC:? 0 rpmb_set_dev_info:1116 RPMB: CID D/TC:? 0 rpmb_set_dev_info:1117 000000009e8b0bd0 d6 01 03 38 38 41 33 39 38 11 eb bf d1 a0 1b 00 D/TC:? 0 legacy_rpmb_init:1162 RPMB INIT: Deriving key I/TC: RPMB: Using generated key F/TC:? 0 k3_sec_proxy_send:131 Verifying the thread F/TC:? 0 k3_sec_proxy_verify_thread:71 Check for thread corruption F/TC:? 0 k3_sec_proxy_verify_thread:88 Check for thread direction F/TC:? 0 k3_sec_proxy_verify_thread:100 Check for thread queue F/TC:? 0 k3_sec_proxy_verify_thread:113 Success F/TC:? 0 k3_sec_proxy_recv:193 Verifying thread F/TC:? 0 k3_sec_proxy_verify_thread:71 Check for thread corruption F/TC:? 0 k3_sec_proxy_verify_thread:88 Check for thread direction F/TC:? 0 k3_sec_proxy_verify_thread:100 Check for thread queue F/TC:? 0 k3_sec_proxy_verify_thread:113 Success I/TC: HUK Initialized D/TC:? 0 legacy_rpmb_init:1176 RPMB INIT: Verifying Key F/TC:? 0 plat_prng_add_jitter_entropy:68 0x89 D/TC:? 0 tee_rpmb_resp_unpack_verify:949 MAC mismatched: E/TC:? 0 legacy_rpmb_init:1191 Verify key failed! 0xffff000f E/TC:? 0 legacy_rpmb_init:1192 Make sure key here matches device key E/LD: copy_section_headers:1135 sys_copy_from_ta_bin E/TC:? 0 ldelf_init_with_ldelf:152 ldelf failed with res: 0xffff000f D/TC:? 0 tee_ta_open_session:696 init session failed 0xffff000f TEEC_Opensession failed with code 0xffff000f origin 0x3