Tool/software:
Hi TI expert,
I'm using the MCU SDK: mcu_plus_sdk_am64x_10_00_00_20. And installed the OTP KeyWriter here: ti.com/secureresources/AM64X-HS-RESTRICTED-SW?
I customized the 'smpk' and 'smek' to generate my X509 certificate, but failed to program it via OTP KeyWriter. Here's the output of the console:
'
Starting Keywriting
Start Enabled VPP
After Enabled VPP
DMSC Firmware Version 10.0.8-v10.00.08_am64x_keywrite
DMSC Firmware revision 0xa
DMSC ABI revision 4.0
keys Certificate found: 0x70018600
Keywriter Debug Response:0x80020
Error occured...
'
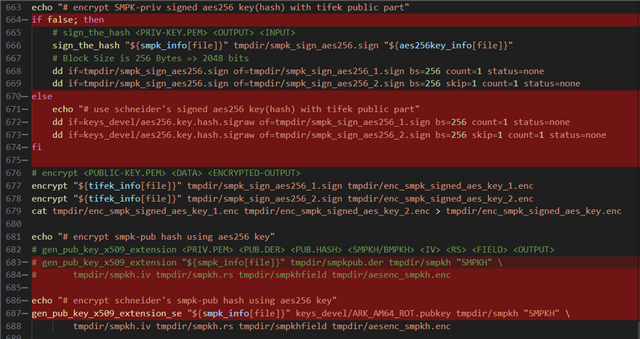
Error bit 19 says 'error validating SMPK singed certificate'. But I've already checked everything, any signing and encryption process looks ok.
I'm wondering what else I do? or Is there any diagnostic tools available to dig what's wrong in the x509 certificate.
I've already successfully validated the certificate by this command:
'openssl x509 -in final_certificate.bin.se -inform DER -noout -text > final_certificate.bin.se.verify.results'