Tool/software:
Hello,
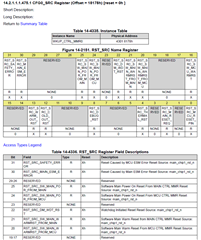
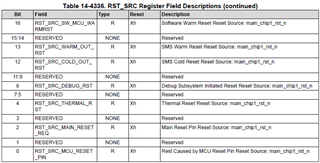
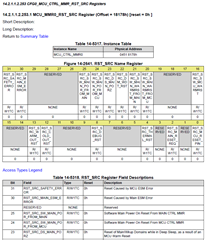
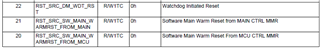
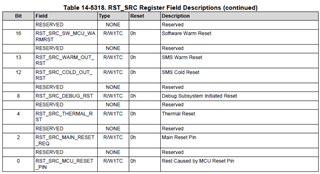
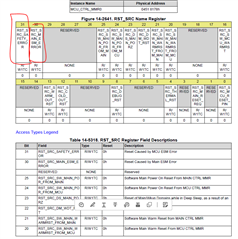
I'm currently working with a AM623 based board running the processor sdk Linux RT version 11.00.09.04. I need to have access to the information of when the last reset was caused by watchdog and, in my research, I found this feature that the rti_wdt driver provides, which is the bootstatus, but it seems it is not available in my OS. I would like to know that should I do to have it enabled so I can have access to the reset reason via Linux.