Other Parts Discussed in Thread: DRA821
Tool/software:
Dear champ,
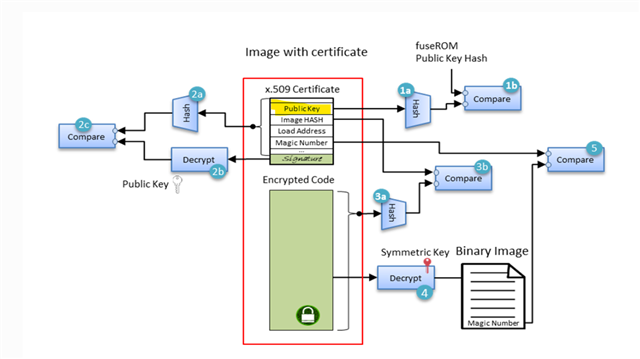
My customer has much experience on security and have done development on TI AM62x and AM64x respectively with secure boot.
Customer uses HSM machine for key store and signing so they have created procedure to get their private key from HSM and work with AM62x and AM64x without problem.
TI sign example uses private key store in computer which is not practice to real user case.
Now the question from customer is about the procedure or sign difference between Jacinto and Sitara product and which could be the missing or different part in creating final image.
OTP key writer has been programmed onto DRA821 successfully per the log been parsed via UART boot.
Please help to check if any step is missing or incorrect if possible.
Secondary, we would like to arrange a remote desktop meeting to check the procedure virtually if we cannot find root cause via e2e.
Feel free to advice any information or possible log you could check. It is a little difficult to describe the issue without much logs. Thanks!
Customer Steps:
- Create J7200 final_certificate.bin (method same as Am62x and Am64x)
- Cover ./pdk_j7200_11_00_00_21/packages/ti/boot/keywriter/x509cert/final_certificate.bin of MCU SDK
- cd pdk_j7200_11_00_00_21/packages/ti/build/
- make keywriter_img_combined BOARD=j7200_evm
- Boot by /home/alvin/ti_j7200_otp/pdk_j7200_11_00_00_21/packages/ti/boot/keywriter/binary/j7200/keywriter_img_combined_j7200_release.tiimage (Uart boot mode)
- get message that J7200 HSFS -> HSSE
-----------------------
SoC ID Header Info:
-----------------------
NumBlocks : [2]
-----------------------
SoC ID Public ROM Info:
-----------------------
SubBlockId : 1
SubBlockSize : 26
DeviceName : j7vcl
DeviceType : HSSE
DMSC ROM Version : [0, 2, 1, 1]
R5 ROM Version : [0, 2, 1, 1]
-----------------------
SoC ID Secure ROM Info:
-----------------------
Sec SubBlockId : 2
Sec SubBlockSize : 166
Sec Prime : 0
Sec Key Revision : 1
Sec Key Count : 2
Sec TI MPK Hash : 04a0cc3e38a1aa0a31fad2423895bfc21ffc7da765dff4aa6e0991fb6e197442ae4d3becef35fe5ed4b63abbcc45c3ecca5ce97ad552fb882fc0eb008c9e5ce2
Sec Cust MPK Hash : e15337a70e7c89e34f000170caaa99db7c7c27fba4eeb51bc14944965a2db965a26c035f3af08900512ee0ab4b815902798029cdc9d674e77004bf5824104fe3
Sec Unique ID : a214e17fefa9e4c55f992e2b4c61b3bbc61c724737fe4075c7bf8e2646d7648d
Q1: Just have to replace file "final_certificate.bin" the keywriter_img_combined_j7200_release.tiimage will burn my public key hash ?
Q2: I build the uboot for HSSE by ti-fs-firmware-j7200_sr2-hs-cert.bin ,ti-fs-firmware-j7200_sr2-hs-enc.bin and sign with the private Key (final_certificate.bin) but it do not work (It had no log message). Steps same as J7200 HSFS.
Q3: How the make sure "Sec Cust MPK Hash" ??
BR, Rich