Tool/software:
I'm working with a customer that is trying secure boot for the first time. My own experience with this is also limited, but I am going to ask if he has followed the steps in our AM64x Secure SDK v3 document as a sanity check.
Currently I have been able to program my public key into my control board using OTP but unable to boot any of the sample projects. I updated the devconfig.mak file to point to my keys and I was able to verify that the sample programs were built using the proper key and certificates by extracting them and comparing hashes. I also used the available python script to parse the UART output of my board, and the public key I expected was programmed into the board for the Sec Cust MPK hash. Although, there are two sets of keys on there and I don’t know what the other one is for or where it came from. It is highlighted in the screen capture below.
The example program I am using to build/boot is the sbl_sd_am64x-evm_r5fss0-0_nortos_ti-arm-clang program since I am currently trying to boot using a SD card. The program builds properly, I take the sbl_sd.Debug.tiimage, rename it to tiboot3.bin and load it to the card, attempt to boot. When it boots up I get absolutely no feedback in the serial console. It just sits there.
As a debugging step, I tried using an "unsigned" image to see what happens and it looked like it tried to boot but then gives me a boot failure which is what I would expect.
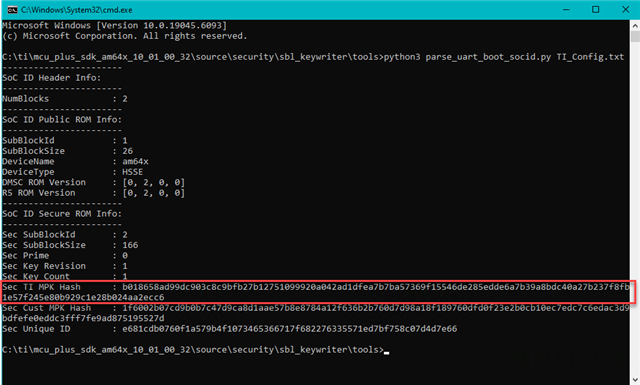
Looking for suggestions on next steps.
Thanks,
Stuart

