Tool/software:
Hi experts,
I am using j784s4_evm with SDK10.
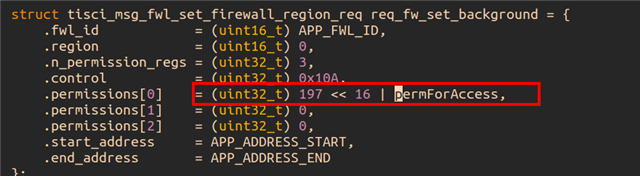
I would like to access TCM memory only from the R5F which it bellongs to for safety reasons.
I would like that other cores (R5F, C7X and A72) couldn't access this memory.
Could you provide any example.
Thanks for your help
Charles