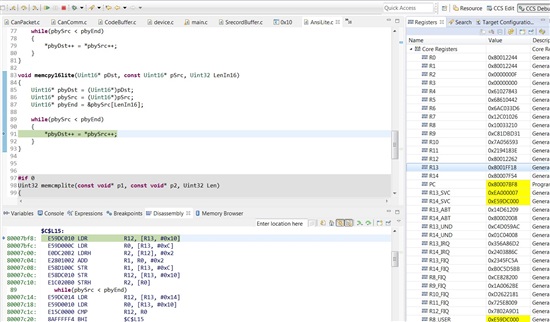
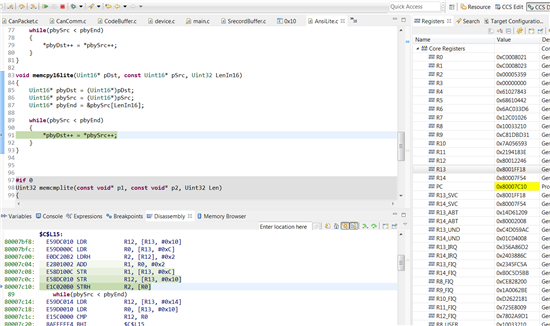
I have a simple function (memcpy16lite()) to copy 16-bit data from Shared RAM to SDRAM.
An odd destination address 0xC0008021 was passed into the function. And when the memcpy16lite() starts executing, the entire processor goes headwire...And an assembly-step through discovered that some malicious assemble code has been generated. See the last assembly line "80007c10: E1C020B0 STRH R2, [R0]", this line tries to write content of 0xC0008023 to some unknown address stored in R2 (R2's content actually is the data loded from copy source which is supposed to write to 0xC0008021, so the actual operation should be the other-way round).
And as soon as I step through that malicious instruction, the processor goes headwrie.
Processor I am using: OMAPL137 ARM
Compiler: Arm v5.1.5 from CCS6.0