Other Parts Discussed in Thread: AFE7700,
Hi Team,
I am using "device.readReg(register address) command to read the register. Is there some GUI where we can read all the register spaces mentioned in "sbau329_AFE77xx_TRM", can you please provide info regardng this?
Also I see that few register maps has common register addresses. How to differentiate the registers between different register map?
Example: 0x2Ch in PLL register map denotes "F[7:0]" and in JESD_SUBCHIP Register Map 0x2Ch is something else. Providing the screenshots from "sbau329_AFE77xx_TRM" for the reference.
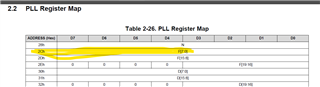
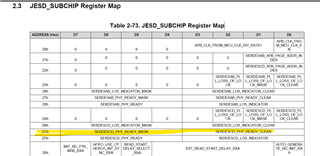
Please help me with these queries
Thanks,
Jaswanth