Tool/software: Code Composer Studio
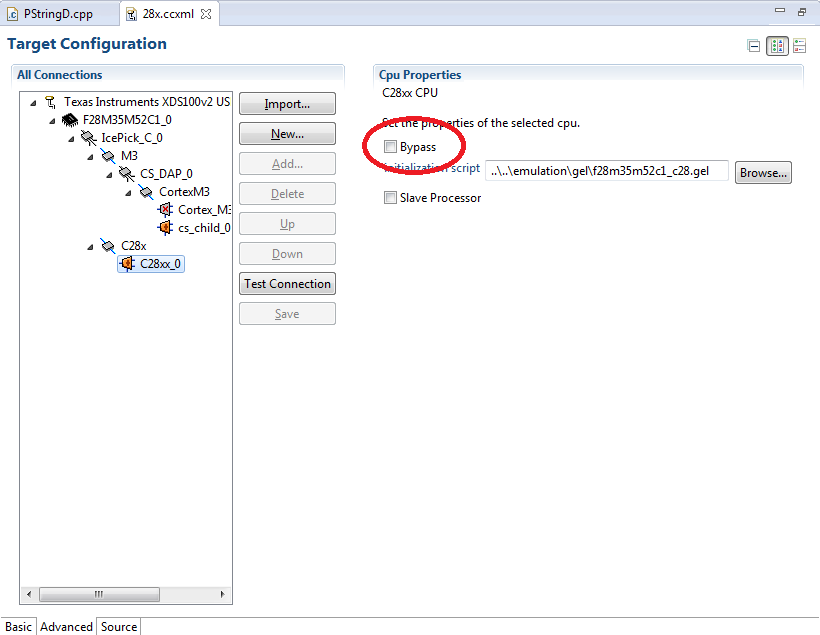
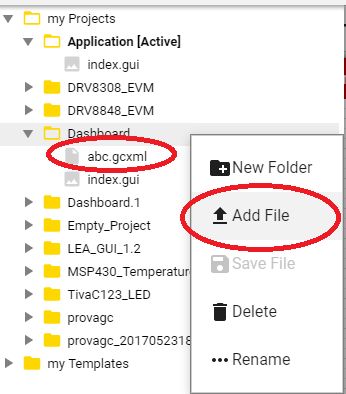
I connot get the new Cloud based Gui Composer to connect to my device and run the Gui directly from the cloud using the TI Cloud Agent Bridge. I am able to create my Gui and then export it as a CCS Desktop View, copy it into the folder and run the application. But this is quite a hassle while I'm still busy developing and testing the Gui. So I have configured an XDS device under the Target Communication Settings in CCS GUI Composer Cloud so that I can program my device and run the Gui from the Cloud Gui composer. When I then try to connect from the Target Communication Settings dialog it just hangs with "Connecting to TI Cloud Agent..." message. I tried to find the TICloudAgent.log file to add it here but I could fine any such file under the path "ti/node/logs/TICloudAgent.log". I'm using Spectrum Digital XDS 200 Debug probe and the Blackhawk XDS 560, does the Cloud agent support these emulators or does it only work with the TI XDS emulators?