Part Number: MSP432E401Y
Hello forum!
A MSP432E401Y should get new firmware from a revolutioin pi using the bsl-scripter.There's an internal network with the pi, the msp432 and some other devices, communicating via modbus. But flashing new firmware doesn't work.
So I build this on my desk: A PC, a rapberry pi and the PCB with the MSP432 are connected via a switch. When the pi only sends the firmware to the MSP, it works.
So additional traffic has to be added. A Browser of the PC shows the http-Site from the MCU, which is updated every ten seconds.Addtional traffic was added this way. And the flashing does not work any more. The output of the Scipter was shown on the terminal:
[ACK_ERROR_MESSAGE]Unknown Error!
Time elapsed of writing 0 bytes : 20.43 seconds
Speed of writing data :0(kB/s)
The receiving of a tftp-package wasn't acknowledget. But why does the flashing over the ethernet only works, if there's no additional traffic on the line?
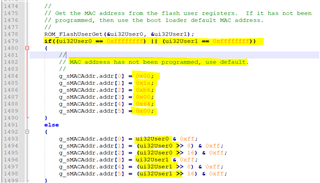
On the mcu there's the bootloader serial_emac_flash.
Thanks in advance,
Guenther