Part Number: TM4C129EKCPDT
Other Parts Discussed in Thread: SYSBIOS,
Hello,
I am trying to post to https://postman-echo.com with reference to code I found in Ti forums. I am getting an error 400 on calling HTTPCli_getResponseStatus(&cli); after a successful post using HTTPCli_sendRequestBody(). Does anyone have previous experience with this? Appreciate your help. Below is my code for your reference.
Thanks.
TI-RTOS for TivaC 2.16.01.14,
XDCtools v 3.32.0.06_core
WolfSSl ver: 3.9.10-stable
/***********HTTPS communication code******************************/
HTTPCli_Params params;
HTTPCli_Struct cli;
HTTPCli_Field fields[3] = {
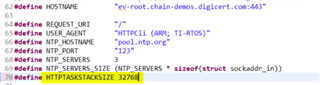
{ HTTPStd_FIELD_NAME_HOST, HOSTNAME },
{ HTTPStd_FIELD_NAME_CONTENT_TYPE, CONTENT_TYPE },
{ NULL, NULL }
};
startNTP();
System_printf("Sending a HTTPS POST request to '%s'\n", HOSTNAME);
System_flush();
TLS_Params_init(&tlsParams);
tlsParams.ca = ca;
tlsParams.calen = calen;
tls = TLS_create(TLS_METHOD_CLIENT_TLSV1_2, &tlsParams, NULL);
if (!tls) {
printError("httpsTask: TLS create failed", -1);
}
HTTPCli_construct(&cli);
HTTPCli_setRequestFields(&cli, fields);
HTTPCli_setResponseFields(&cli, respFields);
ret = HTTPCli_initSockAddr((struct sockaddr *)&addr, "">https://postman-echo.com/POST", 0);
if (ret < 0) {
printError("httpsTask: address resolution failed\n", ret);
}
params.tls = tls;
HTTPCli_Params_init(¶ms);
ret = HTTPCli_connect(&cli, (struct sockaddr *)&addr, HTTPCli_TYPE_TLS, ¶ms);
if (ret < 0) {
printError("httpsTask: connect failed\n", ret);
}
ret = HTTPCli_sendRequest(&cli, HTTPStd_POST, REQUEST_URI, true);
if (ret < 0) {
printError("httpsTask: send failed\n", ret);
}
else
{
System_printf("sendRequest successful\n");
}
ret = HTTPCli_sendField(&cli, HTTPStd_FIELD_NAME_CONTENT_LENGTH, CONTENT_LENGTH, false);
ret = HTTPCli_sendField(&cli, HTTPStd_FIELD_NAME_CONTENT_TYPE, CONTENT_TYPE, true);
if (ret < 0) {
printError("httpTask: send failed\n", ret);
}
else {
System_printf("sendField successful\n");
}
ret = HTTPCli_sendRequestBody(&cli, data, strlen(data));
if (ret < 0) {
printError("httpTask: Variable data couldn't be sent\n", ret);
}
else {
System_printf("Data sent successfully\n");
}
ret = HTTPCli_getResponseStatus(&cli); // here I get an error with code 400