Other Parts Discussed in Thread: SYSCONFIG
Tool/software:
Hello,
This is a follow-up question to the final comment in another thread: 1S-1S-4S Protocol Not Working
In it, Daniel mentioned: "We have actually observed similar behavior in the past and we are currently investigating to resolve this problem." While the original post was about 4S mode, the solution suggested by Daniel was initially created for 8D mode.
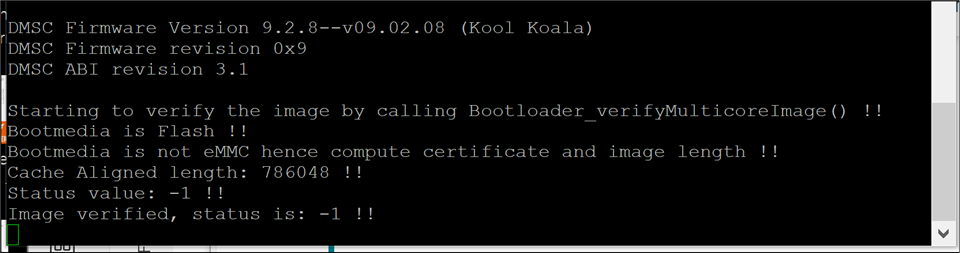
1. I'm interested to know if TI has since observed issues with protocol switching after ROM boot for QSPI devices as well.
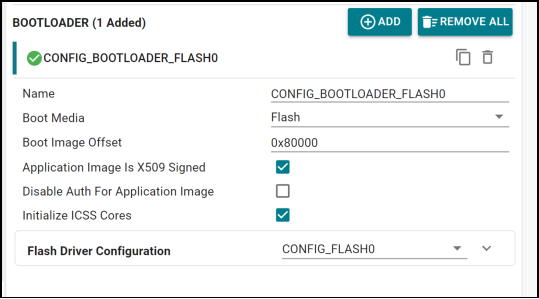
2. Is TI's solution to the 8D problem flashFixUpOspiBoot() and should that function be modified for QSPI protocol?
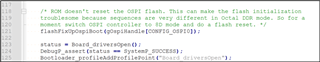
3. Is there another resolution?
Thank you,
Joe