Hi Team,
There is a small probability that it will jump into the ILLEGAL_ISR interrupt before and after the sqrt open operation.
After checking the RPC register, the location is at the point where the sqrt function jumps out to the local variable assignment result. However, the customer would like to know where illegal instructions or overflows can trigger an exception to entry.
Entering an interrupt as shown in the figure below is extremely low and will not be possible until approximately one or two days after running, and if you add some uncorrelated code that changes the length and storage location of the .text section. the problem will not occur.
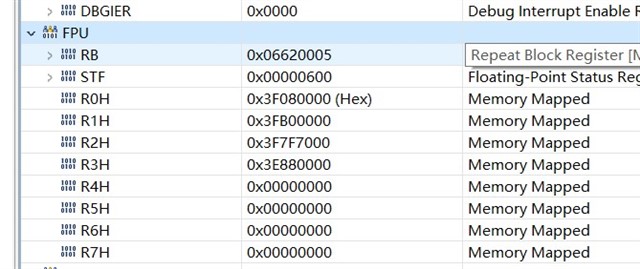
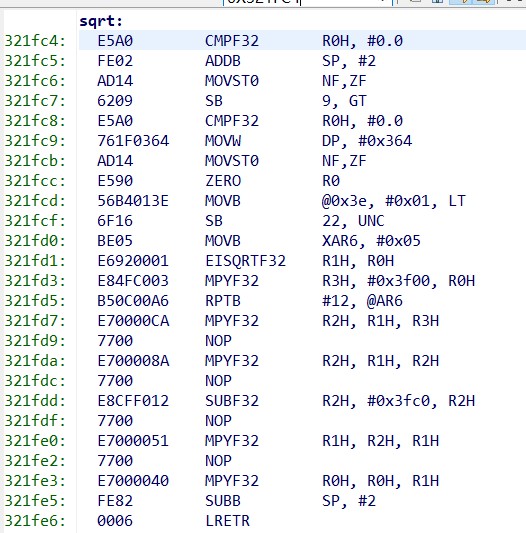
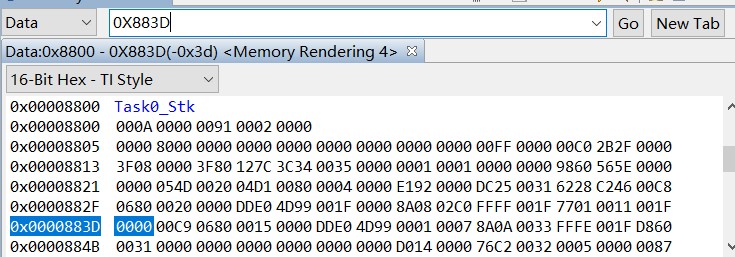
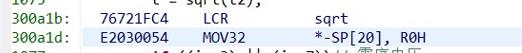
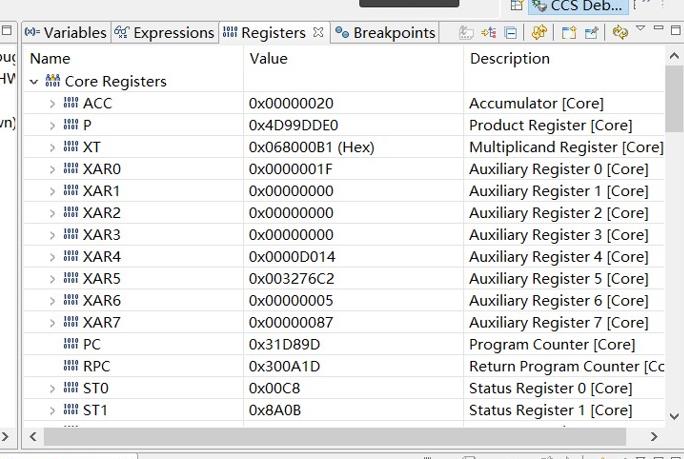
The SP and DP values are as follows:
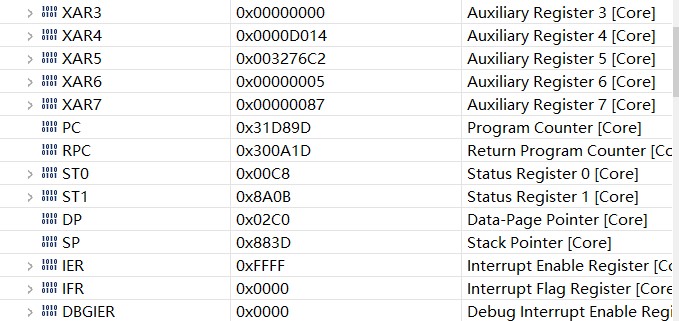
The customer has already troubleshooting the problem of arrays being out of bounds and not having enough stacks, running a μCOS-II, and then opening 2k space for this task. Is the problem likely to be caused by illegal instructions or incorrect addressing modes? Could you help check this case? Thanks.
Best Regards,
Cherry


