Other Parts Discussed in Thread: C2000WARE, SYSCONFIG, UNIFLASH, CCSTUDIO
Tool/software:
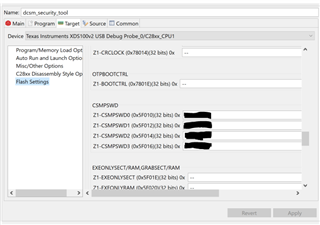
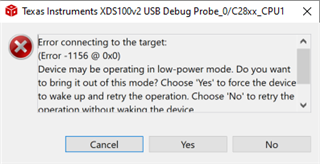
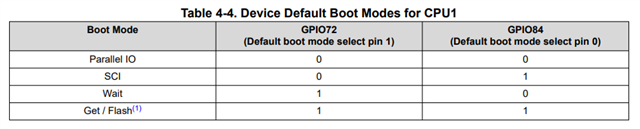
I'm looking to implement a one zone DCSM that protects the memory of the entire device. The preliminary testing is being done on the LAUNCHXL-F28379D. I imported the DCSM Security tool project example from: C2000Ware_4_00_00_00\driverlib\f2837xd\examples\cpu1\dcsm . I updated the sysconfig as shown below and programed the device. It programmed successfully. After the initial program I was unable to program the device again. I put the password in the debug configurations window (shown below), but it still didn't work. I'm getting the error connecting to the target shown below, but when I run the test connection through the target config ccxml, the JTAG DR Integrity scan-test succeeds. I think I'm missing something simple, but I'm not sure what. The design intent is to have all the memory protected on the device once it is released to production. I've looked in the TRM for the device and the DCSM Security Tool app guide, but can't figure out what's wrong.