Other Parts Discussed in Thread: DRA821U, DRA829, TDA4VM, DRA821, TDA4VH
Hi TI
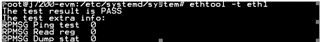
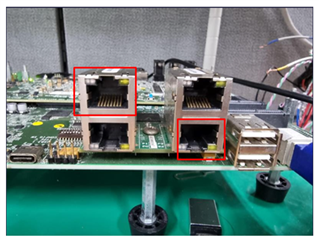
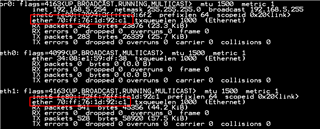
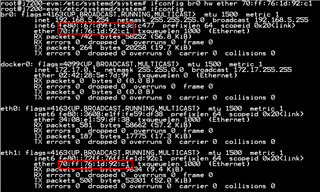
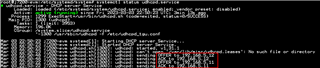
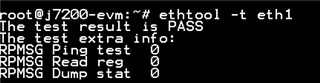
This is an issue reported in SDK 8.2, which is still being reproduced in SDK 8.4.
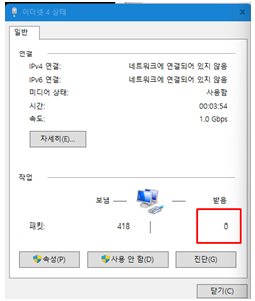
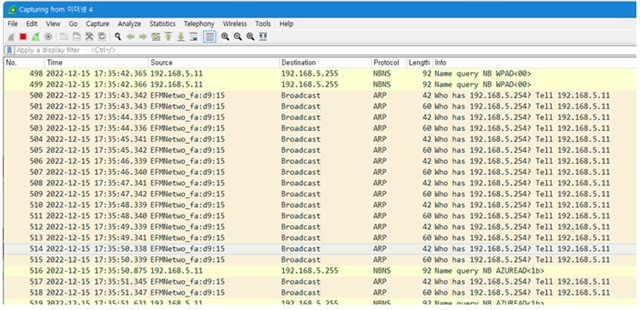
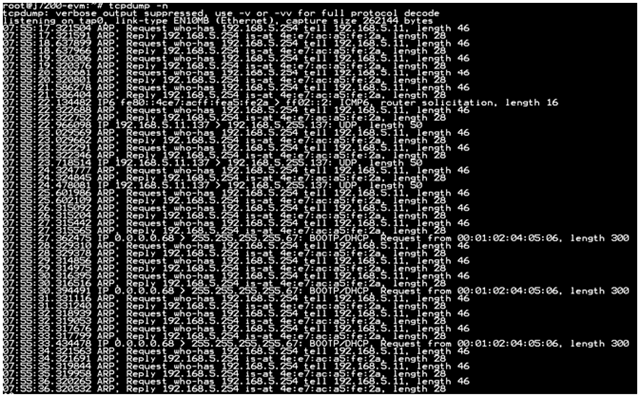
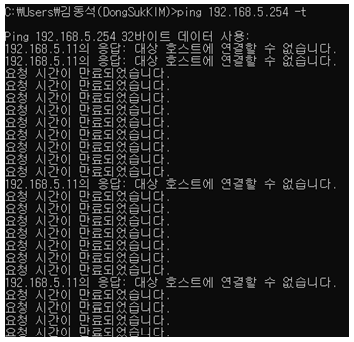
A customer has been reported that they still can not see ip4 related packet and can not get ip from udhcpd.
Please check if the issue is reproducible. and let us know how to fix the problem.
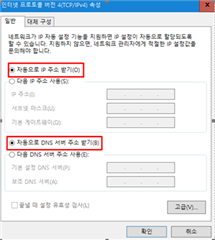
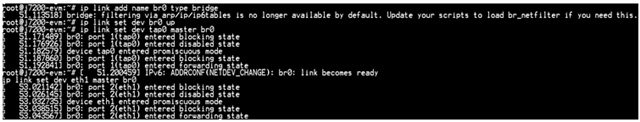
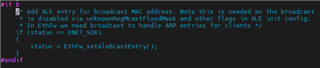
The following is observed during the test.

Regards,
Jack