#1. PSDK 8.03,
#2. General purpose AM62x device (not secure device)
#3. Only use A53.
If did not use atf, optee, M4, R5F, can release or reduce occupied memory in k3-am625-sk.dts reserved-memory? leave more memory for A53 Linux. if yes, please tell us which can be removed or reduced, and how to modify the .dts file.
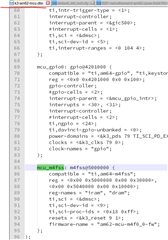
reserved-memory {
#address-cells = <2>;
#size-cells = <2>;
ranges;
secure_tfa_ddr: tfa@9e780000 {
reg = <0x00 0x9e780000 0x00 0x80000>;
alignment = <0x1000>;
no-map;
};
secure_ddr: optee@9e800000 {
reg = <0x00 0x9e800000 0x00 0x01800000>; /* for OP-TEE */
alignment = <0x1000>;
no-map;
};
wkup_r5fss0_core0_dma_memory_region: r5f-dma-memory@9db00000 {
compatible = "shared-dma-pool";
reg = <0x00 0x9db00000 0x00 0xc00000>;
no-map;
};
mcu_m4fss_dma_memory_region: m4f-dma-memory@9cb00000 {
compatible = "shared-dma-pool";
reg = <0x00 0x9cb00000 0x00 0x100000>;
no-map;
};
mcu_m4fss_memory_region: m4f-memory@9cc00000 {
compatible = "shared-dma-pool";
reg = <0x00 0x9cc00000 0x00 0xf00000>;
no-map;
};
lpm_ctx_ddr: lpm-memory@a1000000 {
reg = <0x00 0xa1000000 0x00 0x40000>;
alignment = <0x1000>;
};
};