Other Parts Discussed in Thread: TDA4VH
Hi TI Experts
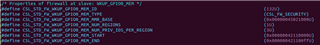
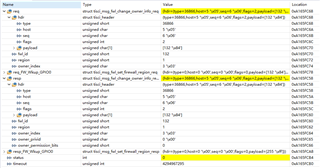
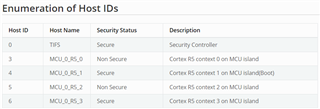
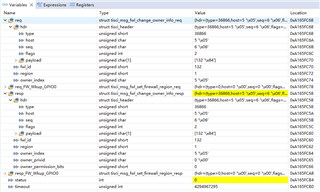
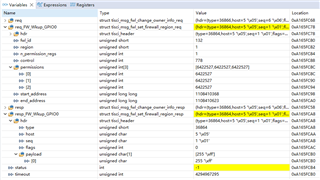
I am trying to use the firewall mechanism to protect the configuration parameters of WKUP_GPIO0 in order that ONLY MCU1_1 can read and write it. I seaching the information for WKUP_GPIO0 in csl_soc_firewalls.h from PDK.