Tool/software:
Hi,
I want to figure out how we load tispl.bin and u-boot.img during SPL startup. For this, I read the following post:
TDA4VM: Where is the R5 SPL source code - Processors forum - Processors - TI E2E support forums
The following is the log of Linux serial port based on SPL startup:
I found the functions board_init_r and spl_Lad_Simple_fit. The function boot_from_devices is called in the function board.init_r, where the log is printed:Trying to boot from.....
Firstly, I added a log in the boot_from_devices function:
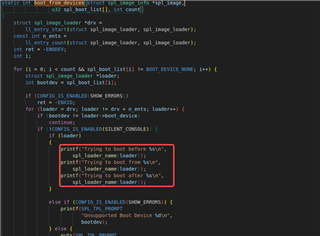
After the make all and make install commands are compiled and started at the board end, I can't find the logs I added. They are the same as the logs when I started earlier. What is the question?
Regards,
Yang

