I am having trouble (could me mental issues....:) initializing an array of floating point variables. Here's my code:
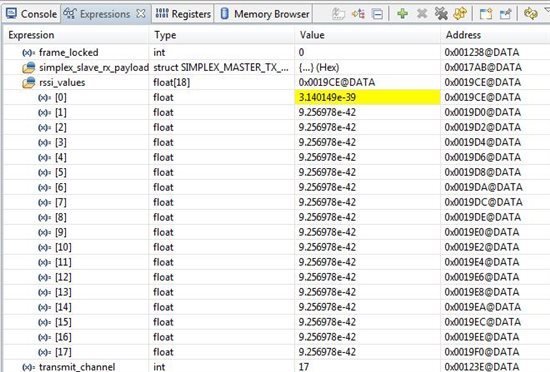
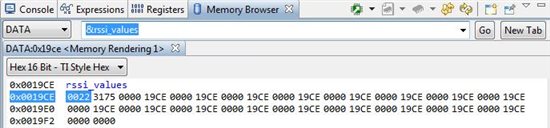
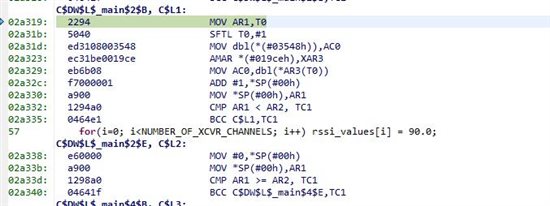
float values[16];
for(i=0; i<16; i++) values[i] = 0;
...which sometimes initializes the array to 0.0 and other times initializes 2.030762e-40, which is pretty close to zero :) Why would it not always initialize to 0.0? When it initializes to something other than zero, writing to the array writes an incorrect value.
Can someone provide some guidance on what may be going wrong?