Other Parts Discussed in Thread: CC3235S, UNIFLASH
We want to use our own certificate.Hence followed the below document.
Vendor Device Authentication With SimpleLink WiFi® Devices
Part Number is CC3220S.
Able to create image using new certificate. While programming give below error.
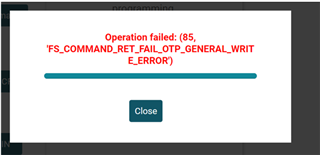
What is the cause of it?