Other Parts Discussed in Thread: Z-STACK
Hi Ryan Brown1 & YK,
It's been a long time,I'm sorry to interrupt,we encounter a strange behaviour on z-stack 3.0.2 with CC2530,that caused our devices(ZR) loss zigbee network(seems like Leave but not received any Leave Request) in next power cycle,as well as known,z-stack 3.0.2 was very stable until now at least 3+ years even if not update,so we don't think the stack have some bug.
So we have to research the BDB specification documents to attemp find some fact. BDB specification from zigbee alliance
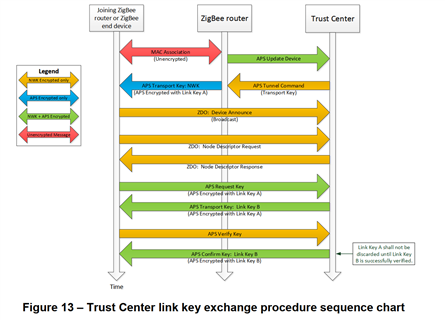
"10.2.6 Receiving new Link Keys" form BDB doc describe the behaviour if node receives a Transport Key contain a TCLK, but have not sent a Request Key, it shall ignore the message,and variable acceptNewUnsolicitedTrustCenterLinkKey
seems like find in ZDSecMgr.c source file but was comment, so we don't know the behavious in z-stack.
attachments is our ota capture with ubiqua,0xE46C and 0xA1D7 loss the zigbee network information in next power cycle.
thanks very much.

