Other Parts Discussed in Thread: UNIFLASH
Team,
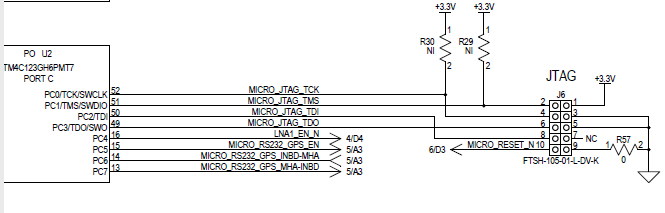
We are having a JTAG lockup issue whenever (using Pinmux) I use pins F0 and F2 as inputs to read power good signals. We now have two boards with locked JTAGs. It was on the second that we discovered that it was when these two pins were added.
I duplicated the problem on the Launchpad Tiva and used UniFlash to unlock it. However, although we are holding the Tiva in reset, when powering it on, we are not able to use the UniFlash tool on our target hardware.
Also, we are connected to our target board using an XDS110 debug probe.
Can you offer any advice or guidance on how to extricate ourselves from this problem?