- Ask a related questionWhat is a related question?A related question is a question created from another question. When the related question is created, it will be automatically linked to the original question.
This thread has been locked.
If you have a related question, please click the "Ask a related question" button in the top right corner. The newly created question will be automatically linked to this question.
MCU SDK: mcu_plus_sdk_am64x_08_05_00_24
Linux SDK: ti-processor-sdk-linux-rt-am64xx-evm-08.06.00.42
Ospi Disk Layout
0x0 - sbl_ospi_linux.tiimage-hs_FS
0x100000 - linux.appimage-hs_FS (built with mcu_plus_sdk_am64x_08_05_00_24/linuxAppimageGen & ti-processor-sdk-linux-rt-am64xx-evm-08.06.00.42 prebuilt-images)
0x300000 - u-boot.img
project sbl_ospi_linux.tiimage-hs_FS:
- I removed code that makes transition to eMMC mode from sbl_ospi_linux project.
- I changed Bootloader offsets with sysconfig which flash_mcu: 0x80000 flash_linux: 0x100000
I am unable to boot my custom board with above configuration
My intent is booting linux.appimage_hs-FS and u-boot from OSPI
But it stuck after SBL
How can I find the problem? (It works with non-custom AM64 GPEVM SR1 with SDK version 08.04)
DMSC Firmware Version 8.5.3--v08.05.03 (Chill Capybar DMSC Firmware revision 0x8 DMSC ABI revision 3.1 [BOOTLOADER_PROFILE] Boot Media : undefined [BOOTLOADER_PROFILE] Boot Image Size : 0 KB [BOOTLOADER_PROFILE] Cores present : m4f0-0 [BOOTLOADER PROFILE] System_init : 26843us [BOOTLOADER PROFILE] Drivers_open : 764668us [BOOTLOADER PROFILE] Board_driversOpen : 0us [BOOTLOADER PROFILE] App_loadImages : 487016us [BOOTLOADER_PROFILE] SBL Total Time Taken : 1438589us Image loading done, switching to application ... Starting linux and RTOS/Baremetal applications
Hello Onur,
Ospi Disk Layout
Here, which application .appimage you have flashed at the default offset of 0x80000?
I removed code that makes transition to eMMC mode from sbl_ospi_linux project.
Do you face the problem if you do not remove this code?
Regads,
Prashant
>> Here, which application .appimage you have flashed at the default offset of 0x80000?
I tried a lot of example app but situation is same (ipc_rpmsg_echo, hello_world (without its a53 parts) uart-echo etc.)
>> I removed code that makes transition to eMMC mode from sbl_ospi_linux project.
Yes it doesn't matter if I remove or not. I am facing same problem evey time.
After Last log message, U-boot spl is not working.
Hi Onur,
I tried a lot of example app but situation is same (ipc_rpmsg_echo, hello_world (without its a53 parts) uart-echo etc.)
Even these appimages are not booting? That is, you do not see any logs from these applications?
These appimages work.
But the problem I am talking is about u-boot.
The linux.appimage.hs_FS is not booting u-boot-spl
I tried both signed (bl31&bl32&u-boot-spl.bin) and unsigned one.
Onur,
Could you please once share the exact changes you have made in the SBL_OSPI_LINUX.
/*
* Copyright (C) 2018-2023 Texas Instruments Incorporated
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
*
* Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
*
* Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the
* distribution.
*
* Neither the name of Texas Instruments Incorporated nor the names of
* its contributors may be used to endorse or promote products derived
* from this software without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
* "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
* LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
* A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
* OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
* LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
* DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
#include <stdlib.h>
#include "ti_drivers_config.h"
#include "ti_drivers_open_close.h"
#include "ti_board_open_close.h"
#include <drivers/sciclient.h>
#include <drivers/bootloader.h>
#include <drivers/pinmux.h>
#include <drivers/gtc.h>
/* Workaround to initialize MMC SD Pinmux (Later will be done in SPL) */
/*
static Pinmux_PerCfg_t gPinMuxMMCSDCfg[] = {
/* MyMMC11 -> MMC1_CMD -> J19 */
{
PIN_MMC1_CMD, PIN_MODE(0) | \
((PIN_PULL_DIRECTION | PIN_INPUT_ENABLE) & (~PIN_PULL_DISABLE))
},
/* MyMMC11 -> MMC1_CLK -> L20 */
{
PIN_MMC1_CLK, PIN_MODE(0) | \
((PIN_PULL_DISABLE | PIN_INPUT_ENABLE) & (~PIN_PULL_DIRECTION))
},
/* MyMMC11 -> MMC1_CLKLB */
{
PIN_MMC1_CLKLB, PIN_MODE(0) | \
((PIN_PULL_DIRECTION | PIN_INPUT_ENABLE) & (~PIN_PULL_DISABLE))
},
/* MyMMC11 -> MMC1_DAT0 -> K21 */
{
PIN_MMC1_DAT0, PIN_MODE(0) | \
((PIN_PULL_DIRECTION | PIN_INPUT_ENABLE) & (~PIN_PULL_DISABLE))
},
/* MyMMC11 -> MMC1_DAT1 -> L21 */
{
PIN_MMC1_DAT1, PIN_MODE(0) | \
((PIN_PULL_DIRECTION | PIN_INPUT_ENABLE) & (~PIN_PULL_DISABLE))
},
/* MyMMC11 -> MMC1_DAT2 -> K19 */
{
PIN_MMC1_DAT2, PIN_MODE(0) | \
((PIN_PULL_DIRECTION | PIN_INPUT_ENABLE) & (~PIN_PULL_DISABLE))
},
/* MyMMC11 -> MMC1_DAT3 -> K18 */
{
PIN_MMC1_DAT3, PIN_MODE(0) | \
((PIN_PULL_DIRECTION | PIN_INPUT_ENABLE) & (~PIN_PULL_DISABLE))
},
/* MyMMC11 -> MMC1_SDCD -> D19 */
{
PIN_MMC1_SDCD, PIN_MODE(0) | \
((PIN_PULL_DIRECTION | PIN_INPUT_ENABLE) & (~PIN_PULL_DISABLE))
},
{PINMUX_END, PINMUX_END}
};
*/
/* In this sample bootloader, we load appimages for RTO/Baremetal and Linux at different offset
i.e the appimage for Linux (for A53) and RTOS/Baremetal (for R5, M4) is flashed at different offset in flash
Here at one flash offset, there is a multi-core .appimage that holds RPRC for M4 and R5
and another .appimage that holds the linux binaries(ATF, OPTEE, A53-SPL) at another offset.
When flashing make sure to flash images to below offset using the flash tool.
RTOS/Baremetal appimage (for R5, M4 cores) flash at offset 0x80000
Linux appimage (for A53) flash at offset 0x280000
*/
/* call this API to stop the booting process and spin, do that you can connect
* debugger, load symbols and then make the 'loop' variable as 0 to continue execution
* with debugger connected.
*/
void loop_forever(void)
{
volatile uint32_t loop = 1;
while(loop)
;
}
int32_t App_loadImages(Bootloader_Handle bootHandle, Bootloader_BootImageInfo *bootImageInfo)
{
int32_t status = SystemP_FAILURE;
if(bootHandle != NULL)
{
status = Bootloader_parseMultiCoreAppImage(bootHandle, bootImageInfo);
/* Load CPUs */
/* Do not load M4 when MCU domain is reset isolated */
if (!Bootloader_socIsMCUResetIsoEnabled())
{
if(status == SystemP_SUCCESS && (TRUE == Bootloader_isCorePresent(bootHandle, CSL_CORE_ID_M4FSS0_0)))
{
bootImageInfo->cpuInfo[CSL_CORE_ID_M4FSS0_0].clkHz = Bootloader_socCpuGetClkDefault(CSL_CORE_ID_M4FSS0_0);
status = Bootloader_loadCpu(bootHandle, &(bootImageInfo->cpuInfo[CSL_CORE_ID_M4FSS0_0]));
}
}
if(status == SystemP_SUCCESS && (TRUE == Bootloader_isCorePresent(bootHandle, CSL_CORE_ID_R5FSS1_0)))
{
bootImageInfo->cpuInfo[CSL_CORE_ID_R5FSS1_0].clkHz = Bootloader_socCpuGetClkDefault(CSL_CORE_ID_R5FSS1_0);
status = Bootloader_loadCpu(bootHandle, &(bootImageInfo->cpuInfo[CSL_CORE_ID_R5FSS1_0]));
}
if(status == SystemP_SUCCESS && (TRUE == Bootloader_isCorePresent(bootHandle, CSL_CORE_ID_R5FSS1_1)))
{
bootImageInfo->cpuInfo[CSL_CORE_ID_R5FSS1_1].clkHz = Bootloader_socCpuGetClkDefault(CSL_CORE_ID_R5FSS1_1);
status = Bootloader_loadCpu(bootHandle, &(bootImageInfo->cpuInfo[CSL_CORE_ID_R5FSS1_1]));
}
/* Assume self boot for either of the cores of R50 cluster */
uint32_t isSelfBoot = FALSE;
if(TRUE == Bootloader_isCorePresent(bootHandle, CSL_CORE_ID_R5FSS0_0))
{
isSelfBoot = TRUE;
}
if(TRUE == Bootloader_isCorePresent(bootHandle, CSL_CORE_ID_R5FSS0_1))
{
isSelfBoot = TRUE;
}
/* Self cores has to be reset together, so check for both */
if(status == SystemP_SUCCESS && (TRUE == isSelfBoot))
{
/* Set clocks for self cluster */
bootImageInfo->cpuInfo[CSL_CORE_ID_R5FSS0_0].clkHz = Bootloader_socCpuGetClkDefault(CSL_CORE_ID_R5FSS0_0);
bootImageInfo->cpuInfo[CSL_CORE_ID_R5FSS0_1].clkHz = Bootloader_socCpuGetClkDefault(CSL_CORE_ID_R5FSS0_1);
/* Reset self cluster, both Core0 and Core 1. Init RAMs and load the app */
status = Bootloader_loadSelfCpu(bootHandle, &bootImageInfo->cpuInfo[CSL_CORE_ID_R5FSS0_0]);
if((status == SystemP_SUCCESS) && (TRUE == Bootloader_socIsR5FSSDual(BOOTLOADER_R5FSS0)))
{
status = Bootloader_loadSelfCpu(bootHandle, &bootImageInfo->cpuInfo[CSL_CORE_ID_R5FSS0_1]);
}
}
}
return status;
}
int32_t App_loadLinuxImages(Bootloader_Handle bootHandle, Bootloader_BootImageInfo *bootImageInfo)
{
int32_t status = SystemP_FAILURE;
if(bootHandle != NULL)
{
status = Bootloader_parseAndLoadLinuxAppImage(bootHandle, bootImageInfo);
if(status == SystemP_SUCCESS)
{
bootImageInfo->cpuInfo[CSL_CORE_ID_A53SS0_0].clkHz = Bootloader_socCpuGetClkDefault(CSL_CORE_ID_A53SS0_0);
status = Bootloader_loadCpu(bootHandle, &(bootImageInfo->cpuInfo[CSL_CORE_ID_A53SS0_0]));
}
}
return status;
}
int32_t App_runCpus(Bootloader_Handle bootHandle, Bootloader_BootImageInfo *bootImageInfo)
{
int32_t status = SystemP_SUCCESS;
/* Do not run M4 when MCU domain is reset isolated */
if (!Bootloader_socIsMCUResetIsoEnabled())
{
if(TRUE == Bootloader_isCorePresent(bootHandle, CSL_CORE_ID_M4FSS0_0))
{
status = Bootloader_runCpu(bootHandle, &(bootImageInfo->cpuInfo[CSL_CORE_ID_M4FSS0_0]));
}
}
if(status == SystemP_SUCCESS && (TRUE == Bootloader_isCorePresent(bootHandle, CSL_CORE_ID_R5FSS1_0)))
{
status = Bootloader_runCpu(bootHandle, &(bootImageInfo->cpuInfo[CSL_CORE_ID_R5FSS1_0]));
}
if(status == SystemP_SUCCESS && (TRUE == Bootloader_isCorePresent(bootHandle, CSL_CORE_ID_R5FSS1_1)))
{
status = Bootloader_runCpu(bootHandle, &(bootImageInfo->cpuInfo[CSL_CORE_ID_R5FSS1_1]));
}
return status;
}
int32_t App_runLinuxCpu(Bootloader_Handle bootHandle, Bootloader_BootImageInfo *bootImageInfo)
{
int32_t status = SystemP_FAILURE;
/* Initialize GTC by enabling using Syscfg */
/* Change the dev stat register to SD card bootmode so that SPL loads uBoot and linux kernel from SD card */
/* SOC_setDevStat(SOC_BOOTMODE_MMCSD); */
/* Enable pinmux for MMCSD (Workaround as MMC SD pinmux is not initialized in A53 SPL) */
/* Pinmux_config(gPinMuxMMCSDCfg, PINMUX_DOMAIN_ID_MAIN); */
status = Bootloader_runCpu(bootHandle, &(bootImageInfo->cpuInfo[CSL_CORE_ID_A53SS0_0]));
return status;
}
int main(void)
{
int32_t status;
Bootloader_profileReset();
Bootloader_socWaitForFWBoot();
#ifndef DISABLE_WARM_REST_WA
/* Warm Reset Workaround to prevent CPSW register lockup */
if (!Bootloader_socIsMCUResetIsoEnabled())
{
Bootloader_socResetWorkaround();
}
#endif
if (!Bootloader_socIsMCUResetIsoEnabled())
{
/* Update devGrp to ALL to initialize MCU domain when reset isolation is
not enabled */
Sciclient_BoardCfgPrms_t boardCfgPrms_pm =
{
.boardConfigLow = (uint32_t)0,
.boardConfigHigh = 0,
.boardConfigSize = 0,
.devGrp = DEVGRP_ALL,
};
status = Sciclient_boardCfgPm(&boardCfgPrms_pm);
/* Enable MCU PLL. MCU PLL will not be enabled by DMSC when devGrp is set
to Main in boardCfg */
Bootloader_enableMCUPLL();
}
Bootloader_socOpenFirewalls();
Bootloader_socNotifyFirewallOpen();
System_init();
Bootloader_profileAddProfilePoint("System_init");
Drivers_open();
Bootloader_profileAddProfilePoint("Drivers_open");
status = Board_driversOpen();
DebugP_assert(status == SystemP_SUCCESS);
Bootloader_profileAddProfilePoint("Board_driversOpen");
status = Sciclient_getVersionCheck(1);
if(SystemP_SUCCESS == status)
{
Bootloader_BootImageInfo bootImageInfo;
Bootloader_Params bootParams;
Bootloader_Handle bootHandle;
Bootloader_BootImageInfo bootImageInfoLinux;
Bootloader_Params bootParamsLinux;
Bootloader_Handle bootHandleLinux;
Bootloader_Params_init(&bootParams);
Bootloader_Params_init(&bootParamsLinux);
Bootloader_BootImageInfo_init(&bootImageInfo);
Bootloader_BootImageInfo_init(&bootImageInfoLinux);
bootHandle = Bootloader_open(CONFIG_BOOTLOADER_FLASH0, &bootParams);
bootHandleLinux = Bootloader_open(CONFIG_BOOTLOADER_FLASH_LINUX, &bootParamsLinux);
if(bootHandle != NULL)
{
status = App_loadImages(bootHandle, &bootImageInfo);
Bootloader_profileAddProfilePoint("App_loadImages");
}
if(SystemP_SUCCESS == status)
{
if(bootHandleLinux != NULL)
{
status = App_loadLinuxImages(bootHandleLinux, &bootImageInfoLinux);
Bootloader_profileAddProfilePoint("App_loadLinuxImages");
}
}
if(SystemP_SUCCESS == status)
{
/* Print SBL log as Linux prints log to the same UART port */
Bootloader_profilePrintProfileLog();
DebugP_log("Image loading done, switching to application ...\r\n");
DebugP_log("Starting linux and RTOS/Baremetal applications\r\n");
UART_flushTxFifo(gUartHandle[CONFIG_UART0]);
}
if(SystemP_SUCCESS == status)
{
status = App_runLinuxCpu(bootHandleLinux, &bootImageInfoLinux);
}
Bootloader_close(bootHandleLinux);
if(SystemP_SUCCESS == status)
{
status = App_runCpus(bootHandle, &bootImageInfo);
}
if(SystemP_SUCCESS == status)
{
status = Bootloader_runSelfCpuWithLinux();
}
Bootloader_close(bootHandle);
}
if(status != SystemP_SUCCESS )
{
DebugP_log("Some tests have failed!!\r\n");
}
Drivers_close();
System_deinit();
return 0;
}
--flash-writer=sbl_prebuilt/am64x-evm/sbl_uart_uniflash.release.hs.tiimage --operation=flash-phy-tuning-data --file=my_sbl_ospi_linux.release.hs.tiimage --operation=flash --flash-offset=0x0 --file=../../examples/drivers/ipc/ipc_rpmsg_echo_linux/am64x-evm/system_freertos/ipc_rpmsg_echo_linux_system.release.appimage.hs --operation=flash --flash-offset=0x80000 --file=./linux.appimage.hs --operation=flash --flash-offset=0x100000
/**
* These arguments were used when this file was generated. They will be automatically applied on subsequent loads
* via the GUI or CLI. Run CLI with '--help' for additional information on how to override these arguments.
* @cliArgs --device "AM64x_beta" --package "ALV" --part "Default" --context "r5fss0-0" --product "MCU_PLUS_SDK@07.03.01"
* @versions {"tool":"1.10.0+2163"}
*/
/**
* Import the modules used in this configuration.
*/
const flash = scripting.addModule("/board/flash/flash", {}, false);
const flash1 = flash.addInstance();
const bootloader = scripting.addModule("/drivers/bootloader/bootloader", {}, false);
const bootloader1 = bootloader.addInstance();
const bootloader2 = bootloader.addInstance();
const ddr = scripting.addModule("/drivers/ddr/ddr", {}, false);
const ddr1 = ddr.addInstance();
const gtc = scripting.addModule("/drivers/gtc/gtc");
const debug_log = scripting.addModule("/kernel/dpl/debug_log");
const mpu_armv7 = scripting.addModule("/kernel/dpl/mpu_armv7", {}, false);
const mpu_armv71 = mpu_armv7.addInstance();
const mpu_armv72 = mpu_armv7.addInstance();
const mpu_armv73 = mpu_armv7.addInstance();
const mpu_armv74 = mpu_armv7.addInstance();
const mpu_armv75 = mpu_armv7.addInstance();
/**
* Write custom configuration values to the imported modules.
*/
bootloader1.appImageOffset = "0x80000";
bootloader1.$name = "CONFIG_BOOTLOADER_FLASH0";
bootloader1.appImageBaseAddress = "0x60080000";
bootloader2.$name = "CONFIG_BOOTLOADER_FLASH_LINUX";
bootloader2.appImageOffset = "0x100000";
/* it's not working with 0x100000 nor 0x300000 */
/* bootloader2.appImageOffset = "0x300000"; */
flash1.$name = "CONFIG_FLASH0";
bootloader1.flashDriver = flash1;
bootloader2.flashDriver = flash1;
flash1.peripheralDriver.$name = "CONFIG_OSPI0";
flash1.peripheralDriver.phyEnable = true;
flash1.peripheralDriver.dmaEnable = true;
flash1.peripheralDriver.inputClkFreq = 166666666;
flash1.peripheralDriver.advanced = true;
ddr1.$name = "CONFIG_DDR0";
const udma = scripting.addModule("/drivers/udma/udma", {}, false);
const udma1 = udma.addInstance({}, false);
udma1.$name = "CONFIG_UDMA0";
flash1.peripheralDriver.udmaDriver = udma1;
debug_log.enableUartLog = true;
debug_log.enableCssLog = false;
debug_log.uartLog.$name = "CONFIG_UART0";
debug_log.uartLog.intrEnable = "DISABLE";
debug_log.uartLog.UART.$assign = "USART0";
mpu_armv71.$name = "CONFIG_MPU_REGION0";
mpu_armv71.size = 31;
mpu_armv71.attributes = "Device";
mpu_armv71.accessPermissions = "Supervisor RD+WR, User RD";
mpu_armv71.allowExecute = false;
mpu_armv72.$name = "CONFIG_MPU_REGION1";
mpu_armv72.size = 15;
mpu_armv72.accessPermissions = "Supervisor RD+WR, User RD";
mpu_armv73.$name = "CONFIG_MPU_REGION2";
mpu_armv73.baseAddr = 0x41010000;
mpu_armv73.size = 15;
mpu_armv73.accessPermissions = "Supervisor RD+WR, User RD";
mpu_armv74.$name = "CONFIG_MPU_REGION3";
mpu_armv74.accessPermissions = "Supervisor RD+WR, User RD";
mpu_armv74.baseAddr = 0x70000000;
mpu_armv74.size = 21;
mpu_armv75.$name = "CONFIG_MPU_REGION4";
mpu_armv75.baseAddr = 0x80000000;
mpu_armv75.size = 31;
/**
* Pinmux solution for unlocked pins/peripherals. This ensures that minor changes to the automatic solver in a future
* version of the tool will not impact the pinmux you originally saw. These lines can be completely deleted in order to
* re-solve from scratch.
*/
flash1.peripheralDriver.OSPI.$suggestSolution = "OSPI0";
flash1.peripheralDriver.OSPI.CLK.$suggestSolution = "ball.N20";
flash1.peripheralDriver.OSPI.CSn0.$suggestSolution = "ball.L19";
flash1.peripheralDriver.OSPI.DQS.$suggestSolution = "ball.N19";
flash1.peripheralDriver.OSPI.D7.$suggestSolution = "ball.M17";
flash1.peripheralDriver.OSPI.D6.$suggestSolution = "ball.N18";
flash1.peripheralDriver.OSPI.D5.$suggestSolution = "ball.P20";
flash1.peripheralDriver.OSPI.D4.$suggestSolution = "ball.P21";
flash1.peripheralDriver.OSPI.D3.$suggestSolution = "ball.M21";
flash1.peripheralDriver.OSPI.D2.$suggestSolution = "ball.M20";
flash1.peripheralDriver.OSPI.D1.$suggestSolution = "ball.M18";
flash1.peripheralDriver.OSPI.D0.$suggestSolution = "ball.M19";
debug_log.uartLog.UART.RXD.$suggestSolution = "ball.D15";
debug_log.uartLog.UART.TXD.$suggestSolution = "ball.C16";
08.04
08.05
08.06
All versions are same `linux.appimage.hs_FS` doesn't boot u-boot-spl
Hi Onur,
Could you please share the binaries you are using to build the linux.appimage. I will test it once on my side & get back to you.
Thanks!
Hi Onur,
I have tested the shared Linux Appimage and it boots fine on my TI AM64x HS-FS EVM board in all the below cases.
I would like to know if you have a TI board with you on which you could run the same binaries. And with your custom board, you have to debug the SBL to know where exactly it is failing. My guess is the SBL execution flow is most probably is failing in the function call Bootloader_verifyMulticoreImage which is reached through App_loadLinuxImages -> Bootloader_parseAndLoadLinuxAppImage -> Bootloader_verifyMulticoreImage.
If you could debug the SBL once, it would greatly help.
Regards,
Prashant
My TI Board is SR1 TMDS64GPEVM and custom board SR2 HS-FS
Unfortunately I don't have opportunity to test with default TI board.
I Debugged SBL but I am unable to continue after below code because there isn't R5-spl (We boot from ospi there isn't sdcard)
int32_t Bootloader_runSelfCpuWithLinux(void)
{
int32_t status = SystemP_SUCCESS;
DebugP_logInfo("All done, reseting self ...\r\n\n");
status = Bootloader_socCpuResetReleaseSelf();
/* control will not reach here */
return status;
}
int32_t Bootloader_socCpuResetReleaseSelf(void)
{
int32_t status = SystemP_SUCCESS;
uint32_t sciclientCpuProcIdCore0, sciclientCpuDevIdCore0;
uint32_t sciclientCpuProcIdCore1 = BOOTLOADER_INVALID_ID, sciclientCpuDevIdCore1 = BOOTLOADER_INVALID_ID;
uint32_t bDualSelfR5F = FALSE;
sciclientCpuProcIdCore0 = Bootloader_socGetSciclientCpuProcId(CSL_CORE_ID_R5FSS0_0);
sciclientCpuDevIdCore0 = Bootloader_socGetSciclientCpuDevId(CSL_CORE_ID_R5FSS0_0);
if(Bootloader_socIsR5FSSDual(BOOTLOADER_R5FSS0) == TRUE)
{
bDualSelfR5F = TRUE;
}
if(bDualSelfR5F == TRUE)
{
sciclientCpuProcIdCore1 = Bootloader_socGetSciclientCpuProcId(CSL_CORE_ID_R5FSS0_1);
sciclientCpuDevIdCore1 = Bootloader_socGetSciclientCpuDevId(CSL_CORE_ID_R5FSS0_1);
}
/*
* DMSC will block until a WFI is issued, thus allowing the following commands
* to be queued so this cluster may be reset by DMSC (queue length is defined in
* "source/drivers/sciclient/include/tisci/{soc}/tisci_sec_proxy.h". If these commands
* were to be issued and executed prior to WFI, the cluster would enter reset and
* bootloader would not be able to tell DMSC to take itself out of reset.
*/
status = Sciclient_procBootWaitProcessorState(sciclientCpuProcIdCore0,
1, 1, 0, 3, 0, 0, 0, SystemP_WAIT_FOREVER);
if(status != SystemP_SUCCESS)
{
DebugP_logError("CPU boot wait command failed for %s\r\n", Bootloader_socGetCoreName(CSL_CORE_ID_R5FSS0_0));
}
if(status==SystemP_SUCCESS)
{
/* hold core0 and core 1 in reset */
if(bDualSelfR5F == TRUE)
{
status = Sciclient_pmSetModuleRst_flags(sciclientCpuDevIdCore1, 1, 0, SystemP_WAIT_FOREVER);
}
/* after this point you cannot single step in CCS */
if(status==SystemP_SUCCESS)
{
status = Sciclient_pmSetModuleRst_flags(sciclientCpuDevIdCore0, 1, 0, SystemP_WAIT_FOREVER);
}
/*
* Un-halt Core1 (Core0 is not halted)
*/
if(bDualSelfR5F == TRUE)
{
if(status==SystemP_SUCCESS)
{
status = Sciclient_procBootSetSequenceCtrl(sciclientCpuProcIdCore1,
0,
TISCI_MSG_VAL_PROC_BOOT_CTRL_FLAG_R5_CORE_HALT,
0,
SystemP_WAIT_FOREVER);
}
}
/* release the CPUs */
if(status==SystemP_SUCCESS)
{
status = Sciclient_procBootReleaseProcessor(sciclientCpuProcIdCore0, 0, SystemP_WAIT_FOREVER);
}
if(bDualSelfR5F == TRUE)
{
if(status==SystemP_SUCCESS)
{
status = Sciclient_procBootReleaseProcessor(sciclientCpuProcIdCore1, 0, SystemP_WAIT_FOREVER);
}
}
/* release the reset for the CPUs */
if(status==SystemP_SUCCESS)
{
status = Sciclient_pmSetModuleRst_flags(sciclientCpuDevIdCore0, 0, 0, SystemP_WAIT_FOREVER);
}
if(bDualSelfR5F == TRUE)
{
if(status==SystemP_SUCCESS)
{
status = Sciclient_pmSetModuleRst_flags(sciclientCpuDevIdCore1, 0, 0, SystemP_WAIT_FOREVER);
}
}
if(status==SystemP_SUCCESS)
{
status = Bootloader_socSecHandover();
}
if(status==SystemP_SUCCESS)
{
/* disable interrupts if enabled */
HwiP_disable();
/* flush all caches */
CacheP_wbInvAll(CacheP_TYPE_ALL);
/* execute wfi, now SYSFW will execute the above commands and reset core0 and core 1 */
__asm__ __volatile__ ("wfi" "\n\t": : : "memory");
}
if(status != SystemP_SUCCESS)
{
DebugP_logError("CPU reset sequence failed for %s\r\n", Bootloader_socGetCoreName(CSL_CORE_ID_R5FSS0_0));
}
}
return status;
}Interestingly, altough my custom board is HS-FS, when I build linux.appimage with the files (bl31 bl32 and u-boot-spl.bin) inside ti-processor-sdk-linux-am64xx-evm-08.00.00.21-Linux-x86-Install.bin It works! But it's not working with 08.06
I am stuck and don't know what to try.
Onur,
Interestingly, altough my custom board is HS-FS, when I build linux.appimage with the files (bl31 bl32 and u-boot-spl.bin) inside ti-processor-sdk-linux-am64xx-evm-08.00.00.21-Linux-x86-Install.bin It works!
This is interesting
About debugging, you did not need to go this far. The function App_loadLinuxImages that I want you to debug comes early in the execution flow. You may refer to the below screen recording.
Here, if you see the status becomes 0 after Bootloader_verifyMulticoreImage function call which means the call was successful. I did the debugging with your shared Linux Appimage. Please let me know what do you see on your end?
Regards,
Prashant
Hi Prashant,
I debugged sbl as you suggested.
The call to bootloader_verifyMulticoreImage was successful and the status variable returned 0.
Additionally I kept debugging sbl until the end.
Up to this point, I have never encountered any errors and the status has always returned successful.
bootloader_soc.c - 959th line:
...
/* after this point you cannot single step in CCS */
if(status==SystemP_SUCCESS)
{
status = Sciclient_pmSetModuleRst_flags(sciclientCpuDevIdCore0, 1, 0, SystemP_WAIT_FOREVER);
}
...But I still get the following logs when I boot the board in ospi_bootmode:
Image loading done, switching to application ... Starting linux RTOS/Baremetal applications NOTICE: BL31: v2.8(release):v2.8-226-g2fcd408663-dirty NOTICE: BL31: 13:4:23 ,Feb 27 2023 20.0 (gcc version 9.2.1 20191025 (GNU Toolchain for the A-profile Architecture 9.2-2019.12 (arm-9.20))) #1 Mar Feb 27 13:47:09 This OP-TEE configuration might be insecure! I/TC: WARNING: Pleocs.io/en/latest/architecture/porting-guidelines.html I/TC: Primary CPU initializing I/TC: SYSFW ABI: 3.1 (firmware rev 0x0008 '8.4.7--v08.04.07 (Jolly Jellyfi') I/TC: HUK Initalized I/TC: Activated SA2UL device I/TC: Enabled firewalls for SA2UL TRNG device I/TC: TRNG initalized I/TC: Drivers initalized I/TC: Primary CPU
Hi Onur,
Are you making sure that you have the boot mode switch set to OSPI boot mode & doing Power-On-Reset everytime?
Regards,
Prashant
Yes, I'm sure the board is in OSPI bootmode.
My bootmode switch combination:
The source of the problem may be u-boot-spl.bin file.
Because as I mentioned before, u-boot-spl.bin compiled with ti-processor-sdk-linux-am64xx-evm-08.00.00.21 worked.
There are differences in the am64x_evm_a53_defconfig files between the two sdk(06 and 00).
Regards,
Hi Onur,
The source of the problem may be u-boot-spl.bin file.
This is what I also suspect now. The prebuilt SPL may not be suited to your custom board.
To confirm this, could you try booting the prebuilt images (tiboot3.bin, tispl.bin & u-boot.img) from the PSDK you used to get the bl31, bl32 & u-bool-spl. You can flash these files at the offsets given below in OSPI.
+-------------+----------+ | tiboot3.bin | 0x0 | +-------------+----------+ | tispl.bin | 0x100000 | +-------------+----------+ | u-boot.img | 0x300000 | +-------------+----------+
Regards,
Prashant
I tested it.
This way spl works !!!
tispl.bin works but linuxappiamge.hs_fs does not.
What could be the problem with my sbl file?
So maybe there is a signing mismatch(between sbl and spl).
Regards,
Hi Onur,
What could be the problem with my sbl file?
I believe you are getting logs from ATF (bl31) & OPTEE (bl32) so there should not be any problem with SBL. Since if SBL had some problem with the Linux Appimage, those logs from ATF & OPTEE shouldn't have come also. The problem seems to be with A53 SPL somehow.
I have one more idea that could be tested and should work.
make u-boot sysfw-image
Regards,
Prashant
Hi Prashant,
I did some tests according to your instructions:
1- It worked as follows:
tiboot3.bin(from prebuilt-images) -> 0x0
tispl.bin(from u-boot_build) -> 0x100000
u-boot.img(from prebuilt-images) -> 0x300000
2- It worked as follows:
tiboot3.bin(from prebuilt-images) -> 0x0
linuxappimage.hs_fs(compiled from prebuilt-images) -> 0x100000
u-boot.img(from prebuilt-images) -> 0x300000
3- It did not work as follows:
sbl_ospi_linux.Debug.hs_fs.tiimage -> 0x0
ipc_rpmsg_echo_linux_system.debug.appimage.hs_fs -> 0x80000
tispl.bin(from u-boot_build) -> 0x100000 (doesn't work if it's an linuxappimage.hs_fs)
u-boot.img(from prebuilt-images) -> 0x300000
Regards,
Hi Onur,
I am not understanding clearly what worked for you.
1/ This is expected.
2/ The tiboot3.bin from PSDK can't boot Linux Appimage. In this testing, what images were exactly flashed? Is the Linux Apppimage generated using the u-boot-spl.bin from u-boot_build worked for you?
3/ Here, the SBL from MCU+ SDK can't boot tispl.bin.
2/ I have tested this again, and by working I mean that I can see that spl is working.
Here Case-2 logs in OSPI bootmode:
U-Boot SPL 2021.01-g2ee8efd654 (Feb 27 2023 - 13:50:10 +0000) EEPROM not available at 80, trying to read at 81 Reading on-board EEPROM at 0x51 failed 1 Reseting on cold boot to work around ErrataID::2331 reseting ... U-Boot SPL 2021.01-g2ee8efd654 (Feb 27 2023 - 13:50:10 +0000) EEPROM not available at 80, trying to read at 81 Reading on-board EEPROM at 0x51 failed 1 SYSFW ABI: 3.1 (firmware rev 0x0008 '8.6.4--v08.06.04 (Chill cappybar') SPL inital stack usage: 13424 bytes Trying to boot from all boot devices ### ERROR ### Please RESET the board ###
Hi Onur,
2- It worked as follows:
tiboot3.bin(from prebuilt-images) -> 0x0
linuxappimage.hs_fs(compiled from prebuilt-images) -> 0x100000
u-boot.img(from prebuilt-images) -> 0x300000
In the 2nd test case, I assume this is tispl.bin instead of linux.appimage.hs_fs. Is it correct?
Also, you have clicked the "This Resolved My Issue" button. I assume this was by mistake and you are still looking for a solution?
Thanks!
I clicked mistakenly, there isn't a way to undo it.
..
The problem still exists. I am looking a solution.
My board hangs after printing ATF&Optee&SYSFW messages.
```
Image loading done, switching to application ...
Starting linux RTOS/Baremetal applications
NOTICE: BL31: v2.8(release):v2.8-226-g2fcd408663-dirty
NOTICE: BL31: 13:4:23 ,Feb 27 2023
20.0 (gcc version 9.2.1 20191025 (GNU Toolchain
for the A-profile Architecture 9.2-2019.12 (arm-9.20)))
#1 Mar Feb 27 13:47:09 This OP-TEE configuration might be insecure!
I/TC: WARNING: Pleocs.io/en/latest/architecture/porting-guidelines.html
I/TC: Primary CPU initializing
I/TC: SYSFW ABI: 3.1 (firmware rev 0x0008 '8.4.7--v08.04.07 (Jolly Jellyfi')
I/TC: HUK Initalized
I/TC: Activated SA2UL device
I/TC: Enabled firewalls for SA2UL TRNG device
I/TC: TRNG initalized
I/TC: Drivers initalized
I/TC: Primary CPU
```
Hi Prashant,
I solved part of the problem.
I mentioned at the beginning that I have a custom board.
There isn't TCA9554APWR(Board presence device circuit ) integrated in my custom board.
I found that part of the u-boot code was hanging because of this integrated.
The code part I mentioned is in u-boot-2021.01+gitAUTOINC+2ee8efd654-g2ee8efd654/board/ti/am64x/evm.c.
Deleting the dm_gpio_get_valu() function line(78) from the "evm.c" file below temporarily solves the problem: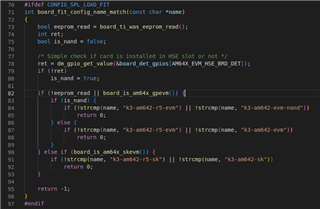
After removing line 78 and the gpio related lines from the code, I recompiled u-boot.
I created linuxappimage.hs_fs in with recompiled u-boot.
I created linuxappimage.hs_fs and spl booted without any problem.
Apart from the above steps, I found another solution.
I compile the U-boot by adding CONFIG_OF_EMBED=y to am64x_evm_a53_defconfig.
I can boot spl without changing anything in u-boot's source code.
With the linuxappimage.hs_fs file I created from this u-boot, spl boots without any problem.
How does CONFIG_OF_EMBED make a difference?
What do you think about the dm_gpio_get_value() part?
Regards,
By the way, could you please undo this post's "This resolved my issue" checkbox?
We didn't even know this component (TCA9554APWR) can cause error like this. There is neither an error message during spl boot nor a mention about TCA9554APWR in any manual&documentation.
Hi Onur,
For the Linux SBLs boot flow, the final u-boot-spl.bin image is created by taking the U-Boot SPL binary without DTBs & concatenating it with the FIT image containing multiple DTBs. This FIT image contains the DTBs for both SK & EVM board. Then, the right DTB is selected at the runtime by calling the board_fit_config_name_match function. You can read more at the below link
However, if CONFIG_OF_EMBED is defined, then the DTB is embedded in the U-Boot SPL binary itself. This ensures the routine, which does the DTB selection at runtime, is not called. That's why, you are not facing issues on enabling CONFIG_OF_EMBED. You can find more info at the below links
https://u-boot.readthedocs.io/en/latest/develop/devicetree/control.html#configuration
https://patchwork.ozlabs.org/project/uboot/patch/1319519734-28704-3-git-send-email-sjg@chromium.org/
Regards,
Prashant