Hi Ti,
I have encountered a freezing issue during the testing of the secure boot process. Upon multiple power cycles, the system freezes at a certain point.
Device Type: HS-SE SR1.1
SDK Version: 08_06_00_12
Test Procedure:
-
Compile SBL
Target compilation is sbl_cust_img_hs.
-
Compile and obtain can boot app
The path for obtaining can boot app is mcusw/binary/can_boot_app_mcu_rtos/bin/j721e_evm.
-
Obtain the image for A72 core.
The path for obtaining the image is pdk_jacinto_08_06_00_31/packages/ti/boot/sbl/tools/BootApp_binaries/linux/j721e_evm_hs.
-
Invoke the script to generate lateapp1/lateapp2.
The path for generating images is pdk_jacinto_08_06_00_31/packages/ti/boot/sbl/example/boot_app/multicore_images/j721e_evm.
-
Obtain TIFS.
The path for obtaining TIFS is pdk_jacinto_08_06_00_31/packages/ti/drv/sciclient/soc/V1.
-
Obtain nor_spi_patterns.bin.
The path for obtaining nor_spi_patterns.bin is packages/ti/board/src/flash/nor/ospi/nor_spi_patterns.bin.
-
Flash the above images into the memory.
-
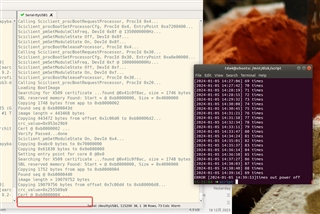
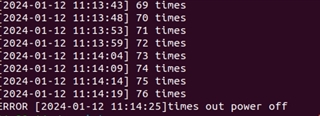
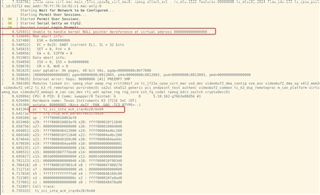
Switch the boot mode to ospi flash boot; conduct multiple power cycles. It is observed that sporadically, the SBL freezes with no LOG output, and after a period of freeze, it automatically resets.
Notes:
No modifications have been made to the code; native TI images are used.
Issues:
- Why does the freezing phenomenon occur, and have you conducted stress tests for secure boot on your end? Please assist in resolving this issue.
- Please help replicate and resolve the issue through the same testing.
- Have you conducted stress testing for secure boot on your end? Can you provide a stress test report for secure boot?
This issue is relatively urgent, so please provide assistance as soon as possible.