Tool/software:
Hi Ti Expert
If we need to boot an HS-FS device (5C silicon) using the Linux SDK 10.00 with customer board, is the following understanding correct:
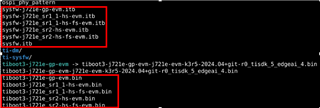
We can use all GP images except for the following two, which must be replaced:
For 5B HS-FS :
-
Replace
sysfw-j721e-gp-evm.itb
➜ withsysfw-j721e_sr1_1-hs-fs-evm.itb -
Replace
tiboot3-j721e-gp-evm.bin
➜ withtiboot3-j721e-sr1_1-hs-fs-evm.bin
All other images (such as tispl.bin, u-boot.img, kernel, DTB, rootfs, etc.) can remain as GP versions.
For 5C HS-FS :
-
Replace
sysfw-j721e_gp-evm.itb
➜ withsysfw-j721e_sr2_0-hs-fs-evm.itb -
Replace
tiboot3-j721e-gp-evm.bin
➜ withtiboot3-j721e-sr2_0-hs-fs-evm.bin
Again, all other images can remain as GP versions.
BRJAY