Hi,
I have been trawling through a number of E2E posts and I can not seem to find a solution to what I'm seeing in by the Secure AISGen binary output
I have a custom board with non-secure OMAP-L138 running SYS-BIOS on both the ARM9 core and DSP core.
I have been developing code on this platform for 6 months with no issue.
I can create binary images (which combine both the ARM and DSP .out files), using AISGen GUI tool, and can load via the UART boot mode or SPI mode.
Now, we are at a point where we have fitted the Secure version of the OMAP-L138 on the same circuit board.
So, I know that I need to make use of the following executable:
"SecureHexAIS_OMAP-L138.exe" and "GenericSecureUartHost.exe"
Note: it is the latest download, OMAPL138_Secure_FlashAndBootUtils V1.06
and created my own ".ini" file.
That has been all well and good, after searching the internet a couple of times.
I now also understand that the DSP core boot first in the secure version of the OMAP, like the OMAP-L137, and I need to pass in the ARM9's entry point using PRUSS, which I have employed the same code used in this post
https://e2e.ti.com/support/dsp/omap_applications_processors/f/42/t/201912
I have also been successful in generating a simply flashing LED image on the ARM with firmware on DSP to pass in the entry point enable the ARM core and again run this over both UART and SPI boot modes.
So I know that I have secure ".ini" file all correctly configured and now I have come to point where I want to generate the binary which combines the DSP and ARM images which both have SYS-BIOS, for the secure OMAP
So essentially taking the same ".out" files used in the non-secure AISGen tool and pass them in via the command line to SecureHexAIS_OMAP-L138.exe.
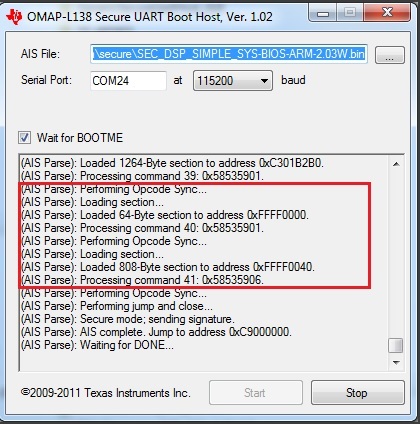
This all work fine, but the image will not boot over UART, it seems to hang at the end (AIS Parse): Waiting for DONE... and never get the Boot completed successfully.
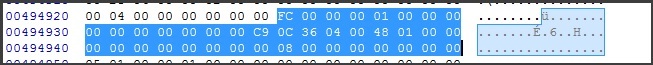
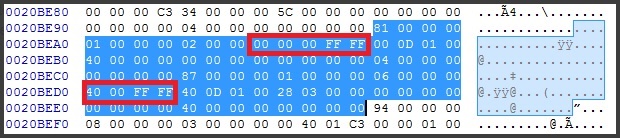
Now investigating the problem further I can something funny going on in the middle of the generated secure binary file.
For some reason when I do a HEX diff between the non-Secure Binary and the Secure Binary using the exact same .out files
I can see that there is additional 0x58535901 command that should not be there, and in fact it is a drive path + strings being inserted and I can not figure out how or why?
Any assistance you provide in addressing this particular problem will be most appreciated.
A second question I have now that the DSP has to passing in the ARM's entry point is, How to define the entry point for the ARM core in the SYS-BIOS app.cfg file?
I have no problem explicitly defining this on the DSP firmware by adding the following lines of code to its app.cfg script
Program.sectMap[".text:_c_int00"] = new Program.SectionSpec();
Program.sectMap[".text:_c_int00"].loadAddress = 0xc9000000;
However doing the exact same thing in the ARM's app.cfg file (with the its correct address) seems to do nothing, as the ".map" file does not seem to change.
Note: I have even tried doing a clean first, to make sure.
And I have read through the link: http://processors.wiki.ti.com/index.php/Accessing_c_int00, but I'm not keen on the idea of "adding a custom linker command (.cmd) file to your project"
Thanking you in advance
Matt