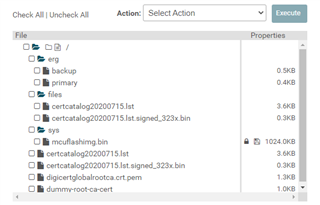
I switched from the dummy-root-ca-cert to the "Use default Trusted Root-Certificate Catalog" certificates, but when I load the image I get:
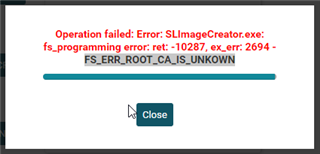
I assume that I need to add the certs manually to the user files. Which files? simplelink_cc32xx_sdk_6_10_00_05\tools\cc32xx_tools\certificate-catalog\certcatalog20200715.lst? Or do I need the bin file as well?
All I see about this is:
6.10 Adding the Trusted Root-Certificate Catalog
The trusted root-certificate is a file provided by TI. The store contains a list of known and trusted root CAs and a
list of revoked certificates. The list of the CAs supported by TI can be found in the CC3x20, CC3x3x
SimpleLink Wi-Fi® Internet-on-a chip
solution built-in security features Application Report.
The ImageCreator installation has a default trusted root-certificate catalog used by the ImageCreator. The
default trusted root-certificate can be overridden by selecting a different file and its signature file. The
ImageCreator has no link to the selected trusted root-certificate original file. To change the trusted root-certificate
content, select a new file.