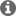Part Number: CC3220
I’m struggling with the CA certificate to set up an secured mqtt TLS communication on CC3220. I know I have a valid CA certificate got from certificate register in windows "DST ROOT CA X3" and saved in mqtt_cert.der/ or .mqtt_cert.Pem" format, those copies were both tested using MQTT.fx to connect to m2m.eclipse.org broker in secured TLS mode and it works perfectly.
however storing this certificate in the CC3220 launchpad caused an issue when trying to set up a secure socket and connect to this socket (look at code below) :
//Step 6: connecting to the server
iStatus = sl_Connect(SSockID, (SlSockAddr_t *) &sAddr, iAddrSize); --> error iStatus =-456 which means:
#define SL_ERROR_BSD_ESECBADCAFILE (-456L) /* error secure level bad CA file */
I think it has something to do with how/where I am storing the certs in the example projects ?!!! Do you have any idea about this issue ??
I respect the documentation that tells how to flash Certs using Uniflash but i have no idea why i'm having this issue ?
* connect to broker Secured mode using TLS
******************************************/
#define SL_TLS_CA_CERT_FILE_NAME "mqtt_cert.der"
#define SERVER_NAME "m2m.eclipse.org"
{
SlSockAddrIn_t sAddr;
int iStatus;
//TODO: to be updated by broker info
//filling the TCP server socket address
g_ulDestinationIp_ = IP_ADDRS;
sAddr.sin_family = SL_AF_INET;
sAddr.sin_port = sl_Htons((unsigned short) mqtt_TLSport);
sAddr.sin_addr.s_addr = sl_Htonl((unsigned int) g_ulDestinationIp_);
iAddrSize = sizeof(SlSockAddrIn_t);
// certificates.PrivateKey = SL_SO_SECURE_FILES_PRIVATE_KEY_FILE_NAME; // mapping private key, 0 file not exist
// certificates.Certificate = SL_SO_SECURE_FILES_CERTIFICATE_FILE_NAME; // mapping certificate, 0 file not exist
// certificates.CA = SL_SO_SECURE_FILES_CA_FILE_NAME/*129*/; // mapping CA, 0 file not exist
// certificates.DH = SL_SO_SECURE_FILES_PEER_CERT_OR_DH_KEY_FILE_NAME; // mapping certificate, 0 file not exist
certificates->SecureFiles[0]=0;
certificates->SecureFiles[1]=0;
certificates->SecureFiles[2]=SL_SO_SECURE_FILES_CA_FILE_NAME;
certificates->SecureFiles[3]=0;
//Set Current Time in the Device (required)
iStatus = set_time();
if(iStatus < 0)
{
UART_PRINT("Unable to set time in the device");
return iStatus;
}
// unsigned int uiIP;
// iStatus = sl_NetAppDnsGetHostByName(g_Host, strlen((const char *)g_Host),(unsigned long*)&uiIP, SL_AF_INET);
//
// if(iStatus < 0)
// {
// UART_PRINT("Device couldn't retreive the host name \n\r");
// return iStatus;
// }
//
// sAddr.sin_family = SL_AF_INET;
// sAddr.sin_port = sl_Htons(mqtt_TLSport);
// sAddr.sin_addr.s_addr = sl_Htonl(uiIP);
// iAddrSize = sizeof(SlSockAddrIn_t);
//A secure socket must be opened by the CC3220 device.
//The sl_Socket() function may be used with the "Protocol" parameter set to SL_SEC_SOCKET (value=100).
SSockID = sl_Socket(SL_AF_INET, SL_SOCK_STREAM, SL_SEC_SOCKET);
if (SSockID < 0)
{
UART_PRINT("Device unable to create secure socket \n\r");
ASSERT_ON_ERROR(SOCKET_CREATE_ERROR);
}
//Step 3:Force specific method (optional)
//By default, SSL 3.0 and TLS 1.2 are enabled. A specific method can be forced by using the sl_SetSockOpt() function.
/* unsigned char ucmethod = SL_SO_SEC_METHOD_SSLV3;
iStatus = sl_SetSockOpt(SSockID, SL_SOL_SOCKET, SL_SO_SECMETHOD, &ucmethod, sizeof(ucmethod));
if (iStatus < 0) {
UART_PRINT("Device couldn't set socket options \n\r");
return iStatus;
}
*/
//Step 4:Force specific cipher (optional)
//By default, the CC3220 will pick the most secure cipher suite that both sides of the connection can support.
//A specific cipher can be forced by using the sl_SetSockOpt() function.
/*unsigned int uiCipher = SL_SEC_MASK_SSL_RSA_WITH_RC4_128_SHA;
if (iStatus < 0) {
UART_PRINT("Device couldn't set socket options \n\r");
return iStatus;
}
*/
//The CC3220 uses files specific to TLS/SSL that may be defined by the user at the application level.
//The files needed are listed below based on the connection type, and must be expressed in the DER format.
//TODO : ADD certificate
// Add certificate: we will test with google certificate at the beginning
//if (certificates != NULL) {
iStatus = sl_SetSockOpt(SSockID, SL_SOL_SOCKET, SL_SO_SECURE_FILES_CA_FILE_NAME, SL_TLS_CA_CERT_FILE_NAME, sizeof(SlSockSecureFiles_t));
{
UART_PRINT("Device couldn't set socket options \n\r");
return iStatus;
}
//Step 5Bis: verify.....
iStatus = sl_SetSockOpt(SSockID, SL_SOL_SOCKET, SL_SO_SECURE_DOMAIN_NAME_VERIFICATION, g_Host, strlen((const char *)g_Host));
if( iStatus < 0 )
{
UART_PRINT("Device couldn't set socket options \n\r");
return iStatus;
}
//}
iStatus = sl_Connect(SSockID, (SlSockAddr_t *) &sAddr, iAddrSize);
if (iStatus < 0)
{
// error
UART_PRINT("Step 6 \n\r");
UART_PRINT("Device couldn't connect to server \n\r");
sl_Close(SSockID);
ASSERT_ON_ERROR(CONNECT_ERROR);
}
}