Hi Charles,
We have set-up the MQTT client without encryption and it just works fine. However, when adding SSL/TLS, it stops working at all. MQTTClient_connect returns -2021 but when debugging more into detail, it turns out that SlNetIfNDK_sockStartSec cannot create the secure socket as it cannot retrieve the certificates.
For security reasons, certificates and keys are not stored in the file system but as arrays inside the firmware, they are passed to SlNet by SlNetIf_loadSecObj:
MQTTClient_Handle mc;
MQTTClient_Params mp;
MQTTClient_ConnParams mcp;
// Virtual file names of the certificates
char *msf[3] = { "ca.pem", "cert.pem", "key.pem" };
//Certificates
const uint8_t sc_sec_ca[] = "-----BEGIN CERTIFICATE-----\n"
"MIIDbTCCAlWgAwIBAgIQOJS41HdZ0aBH554ITPDjmzANBgkqhkiG9w0BAQsFADBJ\n"
...
"3v1WIFze0MYF6XK6IQ6ia6o=\n"
"-----END CERTIFICATE-----";
const uint16_t sc_sec_ca_l = sizeof(sc_sec_ca);
const uint8_t sc_sec_pk[] = "-----BEGIN PRIVATE KEY-----\n"
"MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDMgIYvGyxtmoyK\n"
...
"zVBWLpomdgRuAVM6Zgs8MfaK4zoD/c8KwI5A4iOqCpZseCAu9ohTNMTnB9VeVSkb\n"
"TMZFwZa3TMRvDY7uZVGzEQB2\n"
"-----END PRIVATE KEY-----";
const uint16_t sc_sec_pk_l = sizeof(sc_sec_pk);
uint8_t sc_sec_pc[] = "-----BEGIN CERTIFICATE-----\n"
"MIIFZDCCBEygAwIBAgITEwAAAAxYaQk7gSlDEgAAAAAADDANBgkqhkiG9w0BAQsF\n"
...
"pJ1Ek8d73ZDgO4IAkyhJC0UtwcuMFS51TeSov+THh6A+ewMi34DINw==\n"
"-----END CERTIFICATE-----";
const uint16_t sc_sec_pc_l = sizeof(sc_sec_pc);
// Pass credentials to SlNet
e = SlNetIf_loadSecObj(SLNETIF_SEC_OBJ_TYPE_CERTIFICATE, msf[0], strlen(msf[0]), sc_sec_ca, sc_sec_ca_l, SLNETIF_ID_1);
e = SlNetIf_loadSecObj(SLNETIF_SEC_OBJ_TYPE_CERTIFICATE, msf[1], strlen(msf[1]), sc_sec_pc, sc_sec_pc_l, SLNETIF_ID_1);
e = SlNetIf_loadSecObj(SLNETIF_SEC_OBJ_TYPE_RSA_PRIVATE_KEY, msf[2], strlen(msf[2]), sc_sec_pk, sc_sec_pk_l, SLNETIF_ID_1);
mcp.netconnFlags = MQTTCLIENT_NETCONN_URL | MQTTCLIENT_NETCONN_SEC | MQTTCLIENT_NETCONN_SKIP_DOMAIN_NAME_VERIFICATION | MQTTCLIENT_NETCONN_SKIP_CERTIFICATE_CATALOG_VERIFICATION;
mcp.serverAddr = "...";
mcp.port = 8883;
mcp.method = SLNETSOCK_SEC_METHOD_SSLv3_TLSV1_2;
mcp.cipher = SLNETSOCK_SEC_CIPHER_FULL_LIST;
mcp.nFiles = 3;
mcp.secureFiles = msf;
mp.clientId = mac;
mp.connParams = &mcp;
mp.mqttMode31 = false;
mp.blockingSend = true;
MQTTClient_subscribe(mc, msp, 1);
// ... code to run client ...
MQTTClient_connect(mc);
MQTTClient_connect will always return -2021, if only passing the CA certificate and setting .files to 1 or if passing all 3 files.
SlNetIf_loadSecObj always returns 0 and in debug view you can see that it correctly stores the information. Correctly means that it stores the file name as file name and the data buffer as such: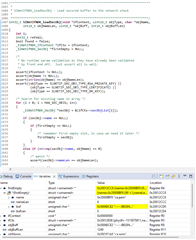
This seems obvious but when having a look at where the error occurs, it is not: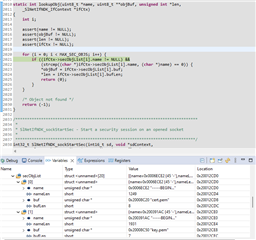
The above image shows the lookupObj function which is called by SlNetIfNDK_sockStartSec to get the certificates. Here you can see that name and buf are inverted, so lookupObj when comparing name with name will never find anything.
I noticed that there used to be a "plugin" for Amazon which should work in a very similarly with a root certificate, a client certificate, and a key. The SDK is not available for download anymore. Is this only because Amazon has changed something on their side so it will not work with them anymore? If yes, acknowledging that we have no intention to use the code for connecting to Amazon but only to compare it to our implementation, could you provide the link?
If you have any other suggestions or ideas regarding this issue, please feel free to comment of course!
Regards
Peter

