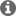Other Parts Discussed in Thread: UNIFLASH, MSP-FET
Hello,
I've been able to follow instructions to disable JTAG on the MSP430FR2xxx device family by writing a value of 0x5555 to JTAG signature 1 and JTAG signature 2. I've also been able to disable the BSL by writing similar signature to 0x5555 and 0x5555. Following this post , since there is a password to enable the BSL but this would be a fixed password, to avoid the risk of the device being able to be unlocked in the field, I understand that I must blow the e-fuse to disable the JTAG, as well as disable the BSL by following the steps mentioned above. I understand that the lock down will only be applied after a reset after this command is applied. When I try to reprogram the tool thereafter, I get an error that 'the device has been secured' and it is unable to be recognised by softwares such as Uniflash.
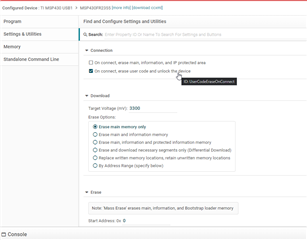
I was able to recover and unlock the device by performing a mass-erase using the TI Uniflash tool and was able to subsequently have the device recogised by Uniflash and re-program the device.
Since I wish to perform these lockdown steps this in my final customer firmware, I want to have the reset functionality also be a part of the firmware itself to reduce the number of extra manufacturing steps required.
However, that means that I need a way to verify that the lock down has already occurred. If it has already occurred once, there is no need to write the memory again and reset the device again (as this would cause a boot loop).
a. How would I apply a device reset from within the MSP430FR2xxx firmware? I'm not aware of a 'reset' command that resets the MCU itself.
b. Looking at documentation, I'm seeing some functions such as 'isLockKeyProgrammed' or 'isFuseBlown'. However these seem to be functions that another device would send the main MCU via the JTAG interface, not something that the main MCU can check within itself. Is the only solution to just read out the two JTAG and BSL signatures and confirm that they are equal to 0x5555 as expected if the device is locked down?
Please let me know.
Warm regards,
Samyukta