Hello,
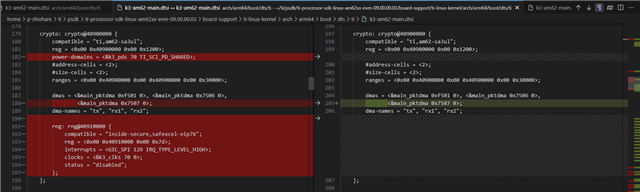
We follow the link provided below to build and implement the hardware crypto accelerator supported on the AM62X platform. The hardware crypto accelerator driver exists and is loaded, but the hardware acceleration does not take effect. Please help determine why:
Hardware encryption acceleration driver:
root@starcharge:/# lsmod |grep sa2ul sa2ul 40960 0 - Live 0xffff800008b7e000 sha512_generic 16384 1 sa2ul, Live 0xffff800008b67000 authenc 16384 1 sa2ul, Live 0xffff800008b5f000
Load the cryptodev driver using the devcrypto engine:
root@starcharge:/# openssl speed -evp aes-128-cbc -engine devcrypto
Engine "devcrypto" set.
Doing AES-128-CBC for 3s on 16 size blocks: 17012594 AES-128-CBC's in 2.99s
Doing AES-128-CBC for 3s on 64 size blocks: 13212821 AES-128-CBC's in 2.98s
Doing AES-128-CBC for 3s on 256 size blocks: 6745574 AES-128-CBC's in 2.99s
Doing AES-128-CBC for 3s on 1024 size blocks: 2382058 AES-128-CBC's in 2.99s
Doing AES-128-CBC for 3s on 8192 size blocks: 339642 AES-128-CBC's in 2.98s
Doing AES-128-CBC for 3s on 16384 size blocks: 171445 AES-128-CBC's in 2.99s
version: 3.1.4
built on: Mon Dec 11 08:59:12 2023 UTC
options: bn(64,64)
compiler: aarch64-buildroot-linux-gnu-gcc -fPIC -pthread -Wa,--noexecstack -D_LARGEFILE_SOURCE -D_LARGEFILE64_SOURCE -D_FILE_OFFSET_BITS=64 -Os -g0 -D_FORTIFY_SOURCE=1 -DOPENSSL_USE_NODELETE -DOPENSSL_PIC -DOPENSSL_BUILDING_OPENSSL -DZLIB -DZLIB_SHARED -DNDEBUG -D_LARGEFILE_SOURCE -D_LARGEFILE64_SOURCE -D_FILE_OFFSET_BITS=64
CPUINFO: OPENSSL_armcap=0xbd
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes 16384 bytes
AES-128-CBC 91037.29k 283765.28k 577547.47k 815795.11k 933673.58k 939449.79k
Remove the cryptodev module:
root@starcharge:/# openssl speed -evp aes-128-cbc
Doing AES-128-CBC for 3s on 16 size blocks: 17042009 AES-128-CBC's in 2.99s
Doing AES-128-CBC for 3s on 64 size blocks: 13235758 AES-128-CBC's in 2.98s
Doing AES-128-CBC for 3s on 256 size blocks: 6743713 AES-128-CBC's in 2.99s
Doing AES-128-CBC for 3s on 1024 size blocks: 2381656 AES-128-CBC's in 2.98s
Doing AES-128-CBC for 3s on 8192 size blocks: 339597 AES-128-CBC's in 2.99s
Doing AES-128-CBC for 3s on 16384 size blocks: 171417 AES-128-CBC's in 2.99s
version: 3.1.4
built on: Mon Dec 11 08:59:12 2023 UTC
options: bn(64,64)
compiler: aarch64-buildroot-linux-gnu-gcc -fPIC -pthread -Wa,--noexecstack -D_LARGEFILE_SOURCE -D_LARGEFILE64_SOURCE -D_FILE_OFFSET_BITS=64 -Os -g0 -D_FORTIFY_SOURCE=1 -DOPENSSL_USE_NODELETE -DOPENSSL_PIC -DOPENSSL_BUILDING_OPENSSL -DZLIB -DZLIB_SHARED -DNDEBUG -D_LARGEFILE_SOURCE -D_LARGEFILE64_SOURCE -D_FILE_OFFSET_BITS=64
CPUINFO: OPENSSL_armcap=0xbd
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes 16384 bytes
AES-128-CBC 91194.70k 284257.89k 577388.14k 818394.54k 930427.63k 939296.36k
Please help to determine why there is basically no change in performance between using and not using cryptodev?
Regards,
Gary