Other Parts Discussed in Thread: TDA4VH
HI, Diwakar
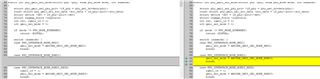
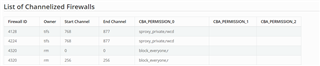
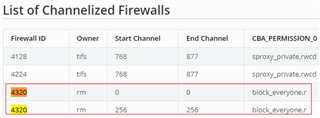
The trace configuration of m4 is modified as follows:
.trace_dst_enables = BOARDCFG_TRACE_DST_UART0,
.trace_src_enables = BOARDCFG_TRACE_SRC_SEC,
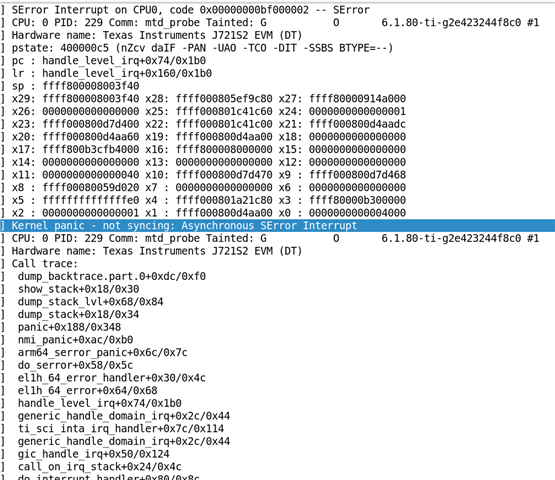
Under this configuration, we reproduced the serror issue twice, and the printout of m4 is as follows:
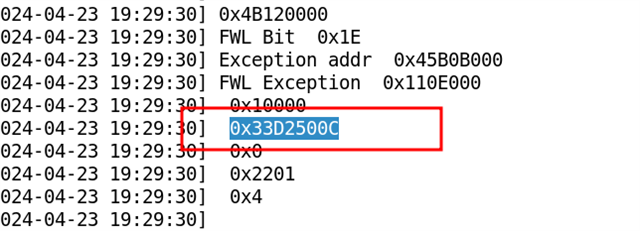
First time:
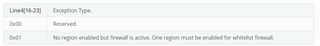
FWL Bit 0x1E
Exception addr 0x45B0B000
FWL Exception 0x110E000
0x10000
0x33D4000C
0x0
0x2201
0x4
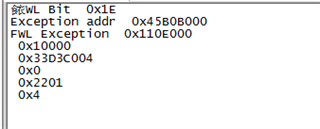
Second time:
FWL Bit 0x1E
Exception addr 0x45B0B000
FWL Exception 0x110E000
0x70000
0x33D3D004
0x0
0x2201
0x4
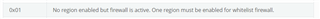
It was discovered that the serror issue was caused by accessing the DMA interrupt configuration register (0x33D4000C and 0x33D3D004).
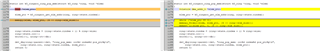
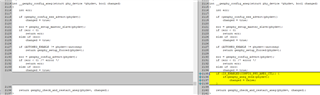
We added the following printout in the kernel:
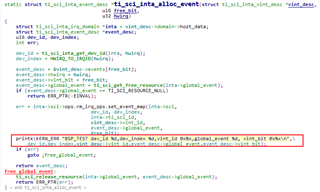
Confirmed to access register 0x33D3D004 when configuring mpu_1_0_ethmac-device-6 and register 0x33D4000C when configuring mpu_1_0_ethmac-device-7
From the above observations, it appears that during the initialization of network DMA, the firewall permissions of DMA interrupt configuration registers occasionally fail to be configured.
Please help to resolve this issue, thank you very much TI.
Best regards
Alex